A long-term cyber-espionage campaign targeting South Asia’s telecom firms has been linked to UAT-7290 – Read More –
Author: Joe-W
Fake ChatGPT and DeepSeek Extensions Spied on Over 1 Million Chrome Users – Hackread – Cybersecurity News, Data Breaches, AI, and More
Security researchers have identified two malicious Chrome extensions recording AI chats. Learn how to identify and remove these tools to protect your privacy. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
A China-nexus threat actor known as UAT-7290 has been attributed to espionage-focused intrusions against entities in South Asia and Southeastern Europe. The activity cluster, which has been active since at least 2022, primarily focuses on extensive technical reconnaissance of target organizations before initiating attacks, ultimately leading to the deployment of malware families such as RushDrop … Read More “China-Linked UAT-7290 Targets Telecoms with Linux Malware and ORB Nodes – The Hacker News” »
‘Elon Musk is playing with fire:’ All the legal risks that apply to Grok’s deepfake disaster – CyberScoop

As collective disgust has continued to build over the widespread generation and sharing of nonconsensual, sexualized deepfakes generated by X’s GrokAI tool, angry onlookers have expressed shock that the activity continues unabated and company owner Elon Musk isn’t being compelled – by either U.S. regulators or law enforcement – to put a halt to the … Read More “‘Elon Musk is playing with fire:’ All the legal risks that apply to Grok’s deepfake disaster – CyberScoop” »
Misconfigurations abused to make phishing emails look like they come from within the organization – Read More –
pcTattletale Founder Bryan Fleming Pleads Guilty in Federal Stalkerware Case – Hackread – Cybersecurity News, Data Breaches, AI, and More

Bryan Fleming, founder of pcTattletale, pleads guilty in a landmark federal spying case. Read how an undercover HSI sting and a data breach ended a decade of illegal stalkerware sales. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
ThreatsDay Bulletin: RustFS Flaw, Iranian Ops, WebUI RCE, Cloud Leaks, and 12 More Stories – The Hacker News

The internet never stays quiet. Every week, new hacks, scams, and security problems show up somewhere. This week’s stories show how fast attackers change their tricks, how small mistakes turn into big risks, and how the same old tools keep finding new ways to break in. Read on to catch up before the next wave … Read More “ThreatsDay Bulletin: RustFS Flaw, Iranian Ops, WebUI RCE, Cloud Leaks, and 12 More Stories – The Hacker News” »
Chainguard, the trusted source for open source, has a unique view into how modern organizations actually consume open source software and where they run into risk and operational burdens. Across a growing customer base and an extensive catalog of over 1800 container image projects, 148,000 versions, 290,000 images, and 100,000 language libraries, and almost half … Read More “The State of Trusted Open Source – The Hacker News” »
Absolute Security claims that full recovery from endpoint-related downtime can take up to a fortnight for most organizations – Read More –
Coolify Discloses 11 Critical Flaws Enabling Full Server Compromise on Self-Hosted Instances – The Hacker News

Cybersecurity researchers have disclosed details of multiple critical-severity security flaws affecting Coolify, an open-source, self-hosting platform, that could result in authentication bypass and remote code execution. The list of vulnerabilities is as follows – CVE-2025-66209 (CVSS score: 10.0) – A command injection vulnerability in the database backup functionality allows any authenticated – Read More – … Read More “Coolify Discloses 11 Critical Flaws Enabling Full Server Compromise on Self-Hosted Instances – The Hacker News” »
Cybersecurity researchers have discovered three malicious npm packages that are designed to deliver a previously undocumented malware called NodeCordRAT. The names of the packages, all of which were taken down as of November 2025, are listed below. They were uploaded by a user named “wenmoonx.” bitcoin-main-lib (2,300 Downloads) bitcoin-lib-js (193 Downloads) bip40 (970 Downloads) “The … Read More “Researchers Uncover NodeCordRAT Hidden in npm Bitcoin-Themed Packages – The Hacker News” »
Cisco has released updates to address a medium-severity security flaw in Identity Services Engine (ISE) and ISE Passive Identity Connector (ISE-PIC) with a public proof-of-concept (PoC) exploit. The vulnerability, tracked as CVE-2026-20029 (CVSS score: 4.9), resides in the licensing feature and could allow an authenticated, remote attacker with administrative privileges to gain access to – … Read More “Cisco Patches ISE Security Vulnerability After Public PoC Exploit Release – The Hacker News” »
The Trump administration decided to leave 66 international organizations, including the GFCE and the European Centre of Excellence for Countering Hybrid Threats – Read More –
A newly discovered vulnerability in authentication platform n8n could allow threat actors to take control of n8n servers – Read More –
With GCAP, the UK government is taking decisive steps towards a safer, more resilient future. – Read More – NCSC Feed
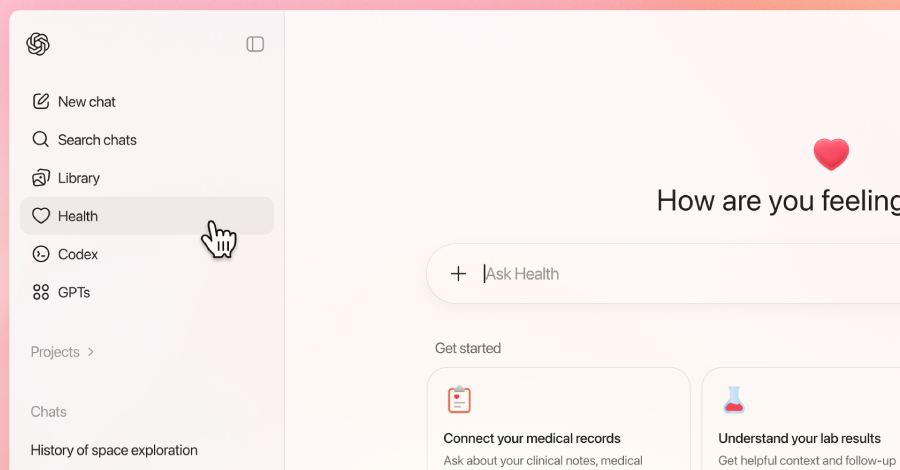
Artificial intelligence (AI) company OpenAI on Wednesday announced the launch of ChatGPT Health, a dedicated space that allows users to have conversations with the chatbot about their health. To that end, the sandboxed experience offers users the optional ability to securely connect medical records and wellness apps, including Apple Health, Function, MyFitnessPal, Weight Watchers, AllTrails, … Read More “OpenAI Launches ChatGPT Health with Isolated, Encrypted Health Data Controls – The Hacker News” »
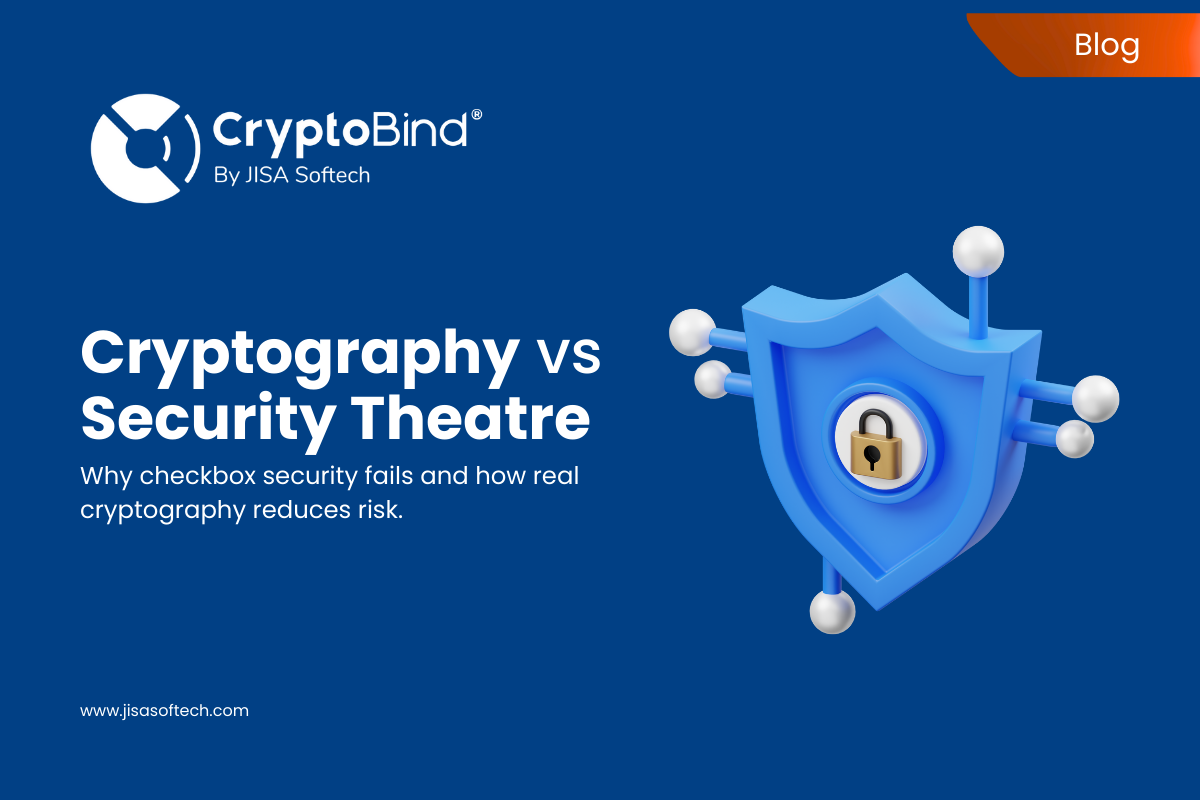
In many organizations, security looks strong on paper. Policies are documented, audits are passed, and compliance dashboards glow reassuringly… The post Cryptography vs Security Theatre appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added two security flaws impacting Microsoft Office and Hewlett Packard Enterprise (HPE) OneView to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. The vulnerabilities are listed below – CVE-2009-0556 (CVSS score: 8.8) – A code injection vulnerability in Microsoft Office – Read … Read More “CISA Flags Microsoft Office and HPE OneView Bugs as Actively Exploited – The Hacker News” »
Romance scammers have apparently discovered astrology… and Taurus is their secret weapon. In episode 449 of “Smashing Security”, we take a look inside an actual romance-fraud handbook – complete with scripts, personality “types”, corporate jargon, and a seven-day plan to get victims from hello to hand over the crypto. Then Lesley “hacks4pancakes” Carhart delivers a … Read More “Smashing Security podcast #449: How to scam someone in seven days – Graham Cluley” »
Researchers warn that a critical vulnerability in n8n, an automation platform that allows organizations to integrate AI agents, workflows and hundreds of other enterprise services, could be exploited by attackers to achieve full control of targeted networks. The maximum-severity vulnerability — CVE-2026-21858 — affects about 100,000 servers globally, according to Cyera, which initially discovered and … Read More “Researchers rush to warn defenders of max-severity defect in n8n – CyberScoop” »
Black Cat Behind SEO Poisoning Malware Campaign Targeting Popular Software Searches – The Hacker News
A cybercrime gang known as Black Cat has been attributed to a search engine optimization (SEO) poisoning campaign that employs fraudulent sites advertising popular software to trick users into downloading a backdoor capable of stealing sensitive data. According to a report published by the National Computer Network Emergency Response Technical Team/Coordination Center of China (CNCERT/CC) … Read More “Black Cat Behind SEO Poisoning Malware Campaign Targeting Popular Software Searches – The Hacker News” »
For the upcoming Pwn2Own Automotive contest, a total of 3 head units have been selected. One of these is the double DIN Kenwood DNR1007XR that offers a variety of functionality such as Android Auto, Apple CarPlay, USB media playback, wireless mirroring and more. This blog post presents photos of the DNR1007XR including highlighting interesting internal … Read More “Breaking Down the Attack Surface of the Kenwood DNR1007XR – Part One – Zero Day Initiative – Blog” »
Lone Hacker Used Infostealers to Access Data at 50 Global Companies – Hackread – Cybersecurity News, Data Breaches, AI, and More

A Hudson Rock report reveals how an Iranian hacker named Zestix breached 50 global companies, including Iberia Airlines and Pickett & Associates, by using stolen passwords and a lack of MFA. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Taiwan endured a year-long intensified cyber offensive from China in 2025, that targeted the government and critical infrastructure — with an increasing focus on the energy and hospital sectors, according to a Taiwan government analysis published this week. Cyberattacks from China rose 6% compared to 2024, the National Security Bureau analysis concluded. Every major sector … Read More “Taiwan blames Chinese ‘cyber army’ for rise in millions of daily intrusion attempts – CyberScoop” »
Malicious Windows packer named pkr_mtsi used as a flexible malware loader in malvertising campaigns – Read More –
Critical n8n Vulnerability (CVSS 10.0) Allows Unauthenticated Attackers to Take Full Control – The Hacker News
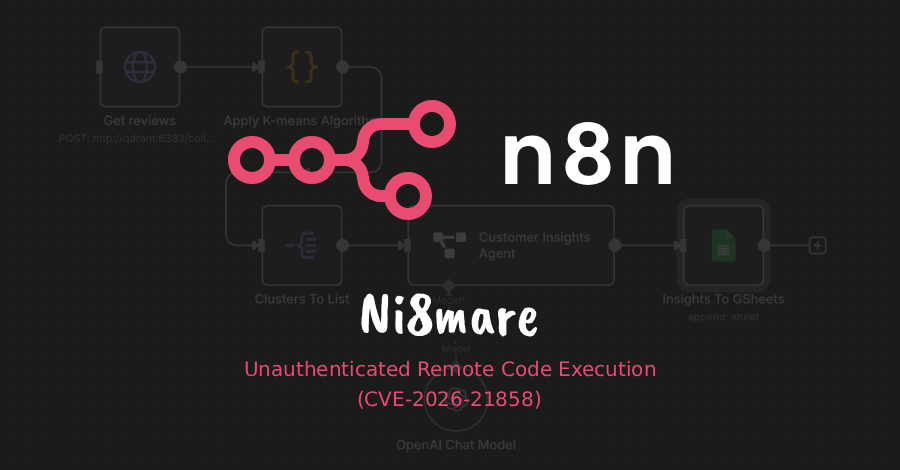
Cybersecurity researchers have disclosed details of yet another maximum-severity security flaw in n8n, a popular workflow automation platform, that allows an unauthenticated remote attacker to gain complete control over susceptible instances. The vulnerability, tracked as CVE-2026-21858 (CVSS score: 10.0), has been codenamed Ni8mare by Cyera Research Labs. Security researcher Dor Attias has been – Read … Read More “Critical n8n Vulnerability (CVSS 10.0) Allows Unauthenticated Attackers to Take Full Control – The Hacker News” »
Veeam has released an update to fix a security flaw in its Backup & Replication software that could let certain users run code on affected systems. The main issue, tracked as CVE-2025-59470, affects all Veeam Backup & Replication version 13 builds, according to a security advisory released Tuesday. Veeam said older product lines, including 12.x … Read More “Veeam issues patch to close critical remote code execution flaw – CyberScoop” »
New Android malware enables unauthorized tap-to-pay transactions without physical access to bank cards – Read More –
Why Legitimate Bot Traffic Is a Growing Security Blind Spot – Hackread – Cybersecurity News, Data Breaches, AI, and More
Security teams have spent years improving their ability to detect and block malicious bots. That effort remains critical.… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Taiwan recorded an average of 2.63 million cyber intrusion attempts to it critical infrastructure per day coming from China in 2025 – Read More –
Lack of visibility and governance around employees using generative AI is resulting in rise in data security risks – Read More –
Veeam has released security updates to address multiple flaws in its Backup & Replication software, including a “critical” issue that could result in remote code execution (RCE). The vulnerability, tracked as CVE-2025-59470, carries a CVSS score of 9.0. “This vulnerability allows a Backup or Tape Operator to perform remote code execution (RCE) as the postgres … Read More “Veeam Patches Critical RCE Vulnerability with CVSS 9.0 in Backup & Replication – The Hacker News” »
Non-human employees are becoming the future of cybersecurity, and enterprises need to prepare accordingly. As organizations scale Artificial Intelligence (AI) and cloud automation, there is exponential growth in Non-Human Identities (NHIs), including bots, AI agents, service accounts and automation scripts. In fact, 51% of respondents in ConductorOne’s 2025 Future of Identity Security Report – Read … Read More “The Future of Cybersecurity Includes Non-Human Employees – The Hacker News” »
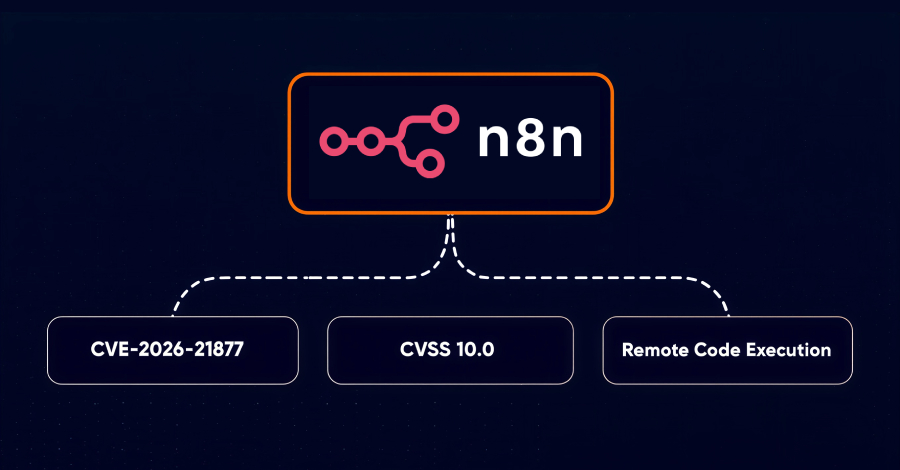
Open-source workflow automation platform n8n has warned of a maximum-severity security flaw that, if successfully exploited, could result in authenticated remote code execution (RCE). The vulnerability, which has been assigned the CVE identifier CVE-2026-21877, is rated 10.0 on the CVSS scoring system. “Under certain conditions, an authenticated user may be able to cause untrusted code … Read More “n8n Warns of CVSS 10.0 RCE Vulnerability Affecting Self-Hosted and Cloud Versions – The Hacker News” »
Webinar: Learn How AI-Powered Zero Trust Detects Attacks with No Files or Indicators – The Hacker News
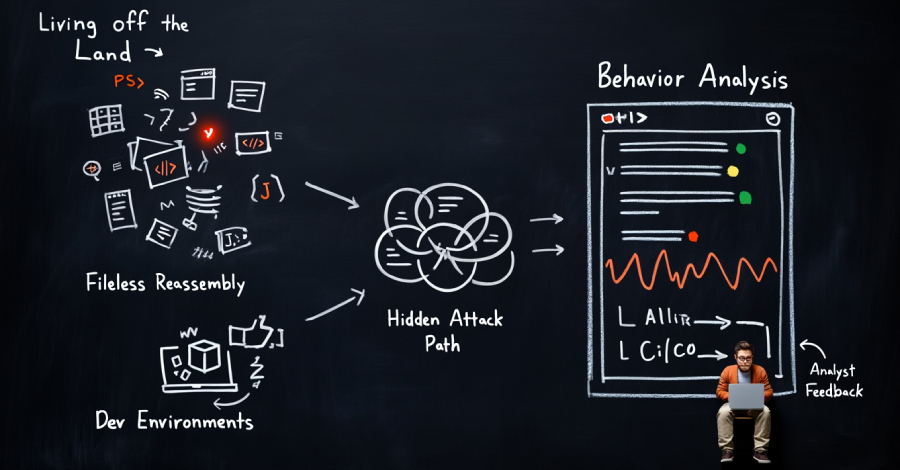
Security teams are still catching malware. The problem is what they’re not catching. More attacks today don’t arrive as files. They don’t drop binaries. They don’t trigger classic alerts. Instead, they run quietly through tools that already exist inside the environment — scripts, remote access, browsers, and developer workflows. That shift is creating a blind … Read More “Webinar: Learn How AI-Powered Zero Trust Detects Attacks with No Files or Indicators – The Hacker News” »
Major Data Breach Hits Company Operating 150 Gas Stations in the US – Hackread – Cybersecurity News, Data Breaches, AI, and More

Texas based Gulshan Management Services, operator of Handi Plus and Handi Stop gas stations, reports a data breach impacting over 377,000 people. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The cybersecurity industry has been battling a talent shortage and skills gap for years. Meanwhile, organizations need a new way to approach risk management proactively and more effectively. AI seems the clear answer to both. Open tech roles are trending down or flat, while demand for AI skills is climbing fast. It’s structural change that … Read More “Why cybersecurity cannot hire its way through the AI era – CyberScoop” »
Threat actors engaging in phishing attacks are exploiting routing scenarios and misconfigured spoof protections to impersonate organizations’ domains and distribute emails that appear as if they have been sent internally. “Threat actors have leveraged this vector to deliver a wide variety of phishing messages related to various phishing-as-a-service (PhaaS) platforms such as Tycoon 2FA,” the … Read More “Microsoft Warns Misconfigured Email Routing Can Enable Internal Domain Phishing – The Hacker News” »
Threat actor “Zestix” was able to breach around 50 firms using infostealers because they lacked multi-factor authentication – Read More –
A hacking collective claims it has disconnected customers of US ISP Brightspeed – Read More –
A breach affecting Manage My Health could have exposed sensitive data for up to 120,000 New Zealand patients – Read More –
A breach affecting Manage My Health could have exposed sensitive data for up to 120,000 New Zealand patients – Read More –
Ongoing Attacks Exploiting Critical RCE Vulnerability in Legacy D-Link DSL Routers – The Hacker News

A newly discovered critical security flaw in legacy D-Link DSL gateway routers has come under active exploitation in the wild. The vulnerability, tracked as CVE-2026-0625 (CVSS score: 9.3), concerns a case of command injection in the “dnscfg.cgi” endpoint that arises as a result of improper sanitization of user-supplied DNS configuration parameters. “An unauthenticated remote attacker … Read More “Ongoing Attacks Exploiting Critical RCE Vulnerability in Legacy D-Link DSL Routers – The Hacker News” »
Millions of Android Powered TVs and Streaming Devices Infected by Kimwolf Botnet – Hackread – Cybersecurity News, Data Breaches, AI, and More

Synthient discovers over 2 million Android TV boxes and smart TVs hijacked by the Kimwolf botnet. Learn how hackers are using home devices to launch DDoS attacks and how you can protect your home network. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The Federal Communications Commission finalized new financial penalties for telecoms that submit false, inaccurate or late reporting to a federal robocalling system. The new regulations, which go into effect Feb. 5, will require providers to recertify every year that their information is accurate in the Robocall Mitigation Database (RMD). It would also impose fines on … Read More “FCC finalizes new penalties for robocall violators – CyberScoop” »
Bitfinex Hack Mastermind Behind $10 Billion Theft Gets Early Release – Hackread – Cybersecurity News, Data Breaches, AI, and More

Ilya Lichtenstein, the man behind the massive 2016 Bitfinex Bitcoin theft, has been released early from prison. Read how the First Step Act and a trail of Walmart gift cards led to this major update in one of the world’s largest crypto thefts. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and … Read More “Bitfinex Hack Mastermind Behind $10 Billion Theft Gets Early Release – Hackread – Cybersecurity News, Data Breaches, AI, and More” »
The CERT Coordination Center (CERT/CC) has disclosed details of an unpatched security flaw impacting TOTOLINK EX200 wireless range extender that could allow a remote authenticated attacker to gain full control of the device. The flaw, CVE-2025-65606 (CVSS score: N/A), has been characterized as a flaw in the firmware-upload error-handling logic, which could cause the device … Read More “Unpatched Firmware Flaw Exposes TOTOLINK EX200 to Full Remote Device Takeover – The Hacker News” »
Ledger Confirms Global-e Breach, Warns Users of Phishing Attempts – Hackread – Cybersecurity News, Data Breaches, AI, and More
Ledger confirms data breach via Global-e partner. Customer info exposed, phishing attacks active. No passwords or crypto recovery phrases leaked. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Two Chrome Extensions Caught Stealing ChatGPT and DeepSeek Chats from 900,000 Users – The Hacker News
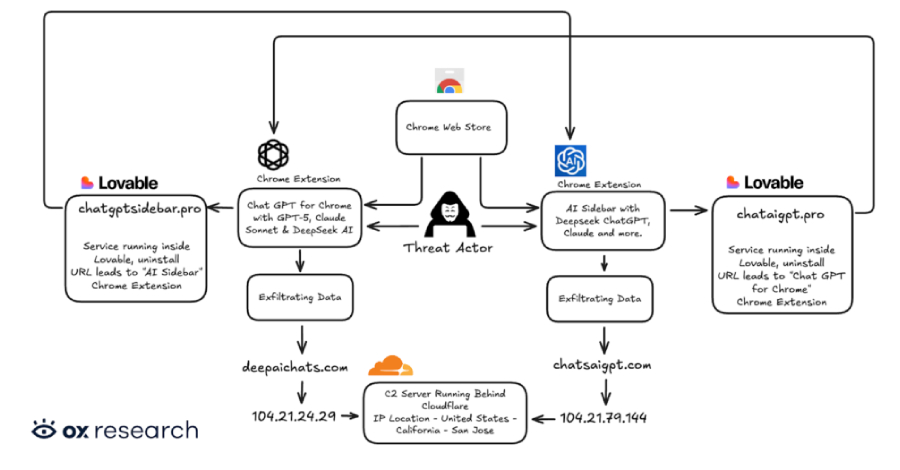
Cybersecurity researchers have discovered two new malicious extensions on the Chrome Web Store that are designed to exfiltrate OpenAI ChatGPT and DeepSeek conversations alongside browsing data to servers under the attackers’ control. The names of the extensions, which collectively have over 900,000 users, are below – Chat GPT for Chrome with GPT-5, Claude Sonnet & … Read More “Two Chrome Extensions Caught Stealing ChatGPT and DeepSeek Chats from 900,000 Users – The Hacker News” »
The CERT Coordination Center (CERT/CC) has disclosed details of an unpatched security flaw impacting TOTOLINK EX200 wireless range extender that could allow a remote authenticated attacker to gain full control of the device. The flaw, CVE-2025-65606 (CVSS score: N/A), has been characterized as a flaw in the firmware-upload error-handling logic, which could cause the device … Read More “Unpatched Firmware Flaw Exposes TOTOLINK EX200 to Full Remote Device Takeover – The Hacker News” »