Multiple vulnerabilities have been discovered in Microsoft products, the most severe of which could allow for remote code execution. Successful exploitation of the most severe of these vulnerabilities could result in an attacker gaining the same privileges as the logged-on user. Depending on the privileges associated with the user, an attacker could then install programs; … Read More “Critical Patches Issued for Microsoft Products, January 13, 2026 – Cyber Security Advisories – MS-ISAC” »
Author: Joe-W
Multiple vulnerabilities have been discovered in Fortinet products, the most severe of which could allow for arbitrary code execution. FortiSandbox is an advanced threat detection solution from Fortinet that uses sandboxing to analyze suspicious files and network traffic for advanced threats like zero-day malware and ransomware. FortiWeb is a web application firewall (WAF) that protects web … Read More “Multiple Vulnerabilities in Fortinet Products Could Allow for Arbitrary Code Execution – Cyber Security Advisories – MS-ISAC” »
Multiple vulnerabilities have been discovered in Google Chrome, the most severe of which could allow for arbitrary code execution. Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated with the user an attacker could then install programs; … Read More “Multiple Vulnerabilities in Google Chrome Could Allow for Arbitrary Code Execution – Cyber Security Advisories – MS-ISAC” »
Microsoft today issued patches to plug at least 113 security holes in its various Windows operating systems and supported software. Eight of the vulnerabilities earned Microsoft’s most-dire “critical” rating, and the company warns that attackers are already exploiting one of the bugs fixed today. January’s Microsoft zero-day flaw — CVE-2026-20805 — is brought to us … Read More “Patch Tuesday, January 2026 Edition – Krebs on Security” »
President Donald Trump re-nominated Sean Plankey to lead the Cybersecurity and Infrastructure Security Agency on Tuesday, after Plankey’s bid for the position ended last year stuck in the Senate. It’s not clear whether or how Plankey’s resubmitted nomination will overcome the hurdles that left many observers convinced his chance of becoming CISA director had likely … Read More “Sean Plankey re-nominated to lead CISA – CyberScoop” »
Microsoft Patch Tuesday addresses 112 defects, including one actively exploited zero-day – CyberScoop

Microsoft’s first security update of 2026 addressed 112 vulnerabilities affecting its products and underlying systems, including one actively exploited zero-day in Desktop Window Manager. The company’s latest Patch Tuesday update marks the second consecutive month with no critical vulnerabilities disclosed. The batch of patches also contains more than 110 CVEs for the second January in … Read More “Microsoft Patch Tuesday addresses 112 defects, including one actively exploited zero-day – CyberScoop” »
A Trump administration official endorsed a slate of congressional bills Tuesday targeting cybersecurity in the energy sector while touting the office’s new emphasis on AI-driven cyber defenses. Meanwhile, Democratic members repeatedly pressed him over the cybersecurity and reliability impacts from thousands of job cuts that have taken place at the Department of Energy over the … Read More “CESER chief touts AI projects as congressional Dems point to federal cuts – CyberScoop” »
Amid budding sentiment in the Trump administration and Congress to expand offensive cyber operations, some lawmakers and experts are warning that the United States needs to get its defenses in order before going too far down that road. A House Homeland Security subcommittee on Tuesday examined how to deter foreign cyberattacks, with an emphasis on … Read More “Hill warning: Don’t put cyber offense before defense – CyberScoop” »
Cybersecurity researchers have discovered a major web skimming campaign that has been active since January 2022, targeting several major payment networks like American Express, Diners Club, Discover, JCB Co., Ltd., Mastercard, and UnionPay. “Enterprise organizations that are clients of these payment providers are the most likely to be impacted,” Silent Push said in a report … Read More “Long-Running Web Skimming Campaign Steals Credit Cards From Online Checkout Pages – The Hacker News” »
In episode 83 of The AI Fix, Graham reveals he’s taken up lying to LLMs, and shows how a journalist exposed AI bluffers with a made-up idiom. Meanwhile Mark invents a “Godwin’s Law” for AI, and explains how to ruin any LLM with humus. Also in this episode, a marriage is declared invalid thanks to … Read More “The AI Fix #83: ChatGPT Health, Victorian LLMs, and the biggest AI bluffers – GRAHAM CLULEY” »
Telegram to Add Warning for Proxy Links After IP Leak Concerns – Hackread – Cybersecurity News, Data Breaches, AI, and More

Telegram will add a warning for proxy links after reports showed they can expose user IP addresses with a single click, bypassing VPN or privacy settings. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
I may be in Tokyo preparing for Pwn2Own Automotive, but that doesn’t stop patch Tuesday from coming. Put aside you broken New Year’s resolutions for just a moment as we review the latest security patches from Adobe and Microsoft. If you’d rather watch the full video recap covering the entire release, you can check out … Read More “The January 2026 Security Update Review – Zero Day Initiative – Blog” »
Multiple vulnerabilities have been discovered in Mozilla products, the most severe of which could allow for arbitrary code execution. Mozilla Firefox is a web browser used to access the Internet. Mozilla Firefox ESR is a version of the web browser intended to be deployed in large organizations. Mozilla Thunderbird is an email client. Mozilla Thunderbird … Read More “Multiple Vulnerabilities in Mozilla Products Could Allow for Arbitrary Code Execution – Cyber Security Advisories – MS-ISAC” »
Flowable 2025.2 Brings Governed Multi-Agent AI Orchestration to Enterprises – Hackread – Cybersecurity News, Data Breaches, AI, and More

Flowable has launched version 2025.2 of its enterprise work orchestration platform, adding support for governed multi-agent AI, impact… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Cybersecurity researchers have disclosed details of a malicious Google Chrome extension that’s capable of stealing API keys associated with MEXC, a centralized cryptocurrency exchange (CEX) available in over 170 countries, while masquerading as a tool to automate trading on the platform. The extension, named MEXC API Automator (ID: pppdfgkfdemgfknfnhpkibbkabhghhfh), has 29 downloads and is still … Read More “Malicious Chrome Extension Steals MEXC API Keys by Masquerading as Trading Tool – The Hacker News” »
SHADOW#REACTOR is a multi-stage Windows malware campaign that stealthily deploys the Remcos RAT using complex infection techniques – Read More –
A high-severity security flaw in the Gogs Git service is being actively exploited, leading to remote code execution – Read More –
Widespread Magecart Campaign Targets Users of All Major Credit Cards – Hackread – Cybersecurity News, Data Breaches, AI, and More
Researchers at Silent Push have exposed a global Magecart campaign stealing credit card data since 2022. Learn how this invisible web-skimming attack targets major networks like Mastercard and Amex, and how to stay safe. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
CrowdStrike is buying Seraphic Security to lock down the browser, where work actually happens – CyberScoop

CrowdStrike announced Tuesday an agreement to acquire Seraphic Security, a browser runtime security provider, in a move that signals growing recognition among cybersecurity firms that traditional protective measures have failed to keep pace with how employees actually work. The acquisition, expected to close during CrowdStrike’s first fiscal quarter of 2027, will integrate Seraphic’s browser-level protection … Read More “CrowdStrike is buying Seraphic Security to lock down the browser, where work actually happens – CyberScoop” »
ServiceNow has addressed a critical security vulnerability in its AI platform that could have allowed unauthenticated users to impersonate legitimate users and perform unauthorized actions, the company disclosed Monday. The flaw, designated CVE-2025-12420 and carrying a severity score of 9.3 out of 10, was discovered by SaaS security firm AppOmni in October. ServiceNow deployed fixes … Read More “ServiceNow patches critical AI platform flaw that could allow user impersonation – CyberScoop” »
CrowdStrike announced Tuesday an agreement to acquire Seraphic Security, a browser runtime security provider, in a move that signals growing recognition among cybersecurity firms that traditional protective measures have failed to keep pace with how employees actually work. The acquisition, expected to close during CrowdStrike’s first fiscal quarter of 2027, will integrate Seraphic’s browser-level protection … Read More “CrowdStrike is buying Seraphic Security to lock down the browser, where work actually happens – CyberScoop” »
AI agents are no longer just writing code. They are executing it. Tools like Copilot, Claude Code, and Codex can now build, test, and deploy software end-to-end in minutes. That speed is reshaping engineering—but it’s also creating a security gap most teams don’t see until something breaks. Behind every agentic workflow sits a layer few … Read More “[Webinar] Securing Agentic AI: From MCPs and Tool Access to Shadow API Key Sprawl – The Hacker News” »
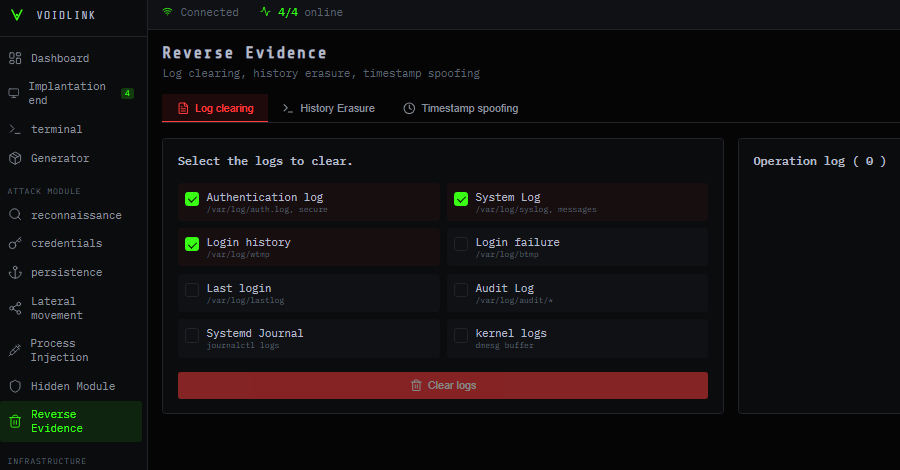
Detected by Check Point researchers, VoidLink is a sophisticated malware framework that can be used to implant malware in the most common cloud environments – Read More –
Cybersecurity researchers issue warning over a surge in attacks designed to trick Facebook users into handing over login credentials – Read More –
Cybersecurity researchers have disclosed details of a previously undocumented and feature-rich malware framework codenamed VoidLink that’s specifically designed for long-term, stealthy access to Linux-based cloud environments According to a new report from Check Point Research, the cloud-native Linux malware framework comprises an array of custom loaders, implants, rootkits, and modular – Read More – The … Read More “New Advanced Linux VoidLink Malware Targets Cloud and container Environments – The Hacker News” »
Q4 2025 Malware Trends: Telegram Backdoor, Banking Trojans Surge, Joker Returns to Google Play – Hackread – Cybersecurity News, Data Breaches, AI, and More
Telegram mods spread a powerful Android backdoor as banking trojans surge and Joker malware resurfaces on Google Play in Q4 2025, says Doctor Web. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
ServiceNow Patches Critical AI Platform Flaw Allowing Unauthenticated User Impersonation – The Hacker News

ServiceNow has disclosed details of a now-patched critical security flaw impacting its ServiceNow AI Platform that could enable an unauthenticated user to impersonate another user and perform arbitrary actions as that user. The vulnerability, tracked as CVE-2025-12420, carries a CVSS score of 9.3 out of 10.0 “This issue […] could enable an unauthenticated user to … Read More “ServiceNow Patches Critical AI Platform Flaw Allowing Unauthenticated User Impersonation – The Hacker News” »
Old Playbook, New Scale: While defenders are chasing trends, attackers are optimizing the basics The security industry loves talking about “new” threats. AI-powered attacks. Quantum-resistant encryption. Zero-trust architectures. But looking around, it seems like the most effective attacks in 2025 are pretty much the same as they were in 2015. Attackers are exploiting the same … Read More “What Should We Learn From How Attackers Leveraged AI in 2025? – The Hacker News” »
Cybersecurity researchers have disclosed details of a new campaign dubbed SHADOW#REACTOR that employs an evasive multi-stage attack chain to deliver a commercially available remote administration tool called Remcos RAT and establish persistent, covert remote access. “The infection chain follows a tightly orchestrated execution path: an obfuscated VBS launcher executed via wscript.exe invokes a – Read … Read More “New Malware Campaign Delivers Remcos RAT Through Multi-Stage Windows Attack – The Hacker News” »
Hexaware Partners with AccuKnox for Cloud Security Services – Hackread – Cybersecurity News, Data Breaches, AI, and More

Menlo Park, USA, 13th January 2026, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Silent Push has discovered a new Magecart campaign targeting six major payment network providers that has been running since 2022 – Read More –
Lawmakers want the security industry to help them scrutinize the Cyber Security and Resilience Bill – Read More –
Have you ever stolen data, traded a hacking tool, or just lurked on a dark web forum believing that you are anonymous? If so, I might have some unsettling news for you. Read more in my article on the Hot for Security blog. – Read More – GRAHAM CLULEY
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has warned of active exploitation of a high-severity security flaw impacting Gogs by adding it to its Known Exploited Vulnerabilities (KEV) catalog. The vulnerability, tracked as CVE-2025-8110 (CVSS score: 8.7), relates to a case of path traversal in the repository file editor that could result in code … Read More “CISA Warns of Active Exploitation of Gogs Vulnerability Enabling Code Execution – The Hacker News” »
The Real Cost of a Data Breach: Why Data Protection Is Now a Boardroom Priority – JISA Softech Pvt Ltd

Organizations will start and possibly end with regulatory fines when discussing the cost of data breach. Although the fines imposed on the… The post The Real Cost of a Data Breach: Why Data Protection Is Now a Boardroom Priority appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
Spanish police disrupt Black Axe, arrest alleged leaders in action spanning four cities – CyberScoop

Authorities arrested 34 alleged cybercriminals in Spain, including some leaders of Black Axe, a transnational criminal organization responsible for adversary-in-the-middle scams such as business email compromise, money laundering and vehicle trafficking, the Spanish National Police said Friday. A coordinated law enforcement operation that fanned out to Seville, Madrid, Malaga and Barcelona significantly disrupted the group’s … Read More “Spanish police disrupt Black Axe, arrest alleged leaders in action spanning four cities – CyberScoop” »
Russian BlueDelta (Fancy Bear) Uses PDFs to Steal Logins in Just 2 Seconds – Hackread – Cybersecurity News, Data Breaches, AI, and More
New research from Recorded Future reveals how Russian state hackers (BlueDelta) are using fake Microsoft and Google login portals to steal credentials. The campaign involves using legitimate PDF lures from GRC and EcoClimate to trick victims. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Fake Employee Reports Spread Guloader and Remcos RAT Malware – Hackread – Cybersecurity News, Data Breaches, AI, and More

Scammers are using fake October 2025 performance reviews to trick staff into installing Guloader and Remcos RAT malware. Learn how to identify this threat and protect your personal data from remote hackers. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
5 Best Secure Container Images for Modern Applications (2026) – Hackread – Cybersecurity News, Data Breaches, AI, and More

Secure container images are now essential for modern apps. These five options help teams reduce risk, cut patching effort, and improve long-term security. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The UK’s top internet regulator opened a formal investigation into social media network X after users, with the help of its AI chatbot Grok, flooded the site with nonconsensual, AI-manipulated nude and undressed photos of real people. On Monday, the Office of Communications (Ofcom), which regulates internet and telecommunications companies, said the investigation will determine … Read More “British regulator Ofcom opens investigation into X – CyberScoop” »
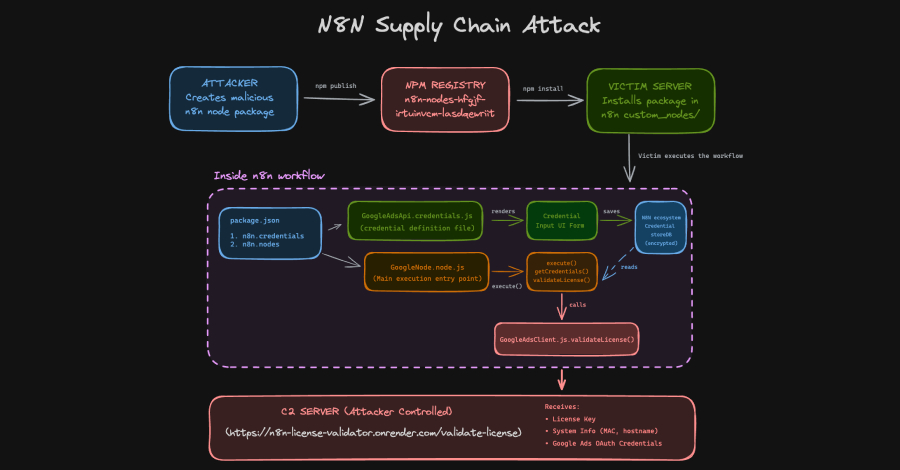
Threat actors have been observed uploading a set of eight packages on the npm registry that masqueraded as integrations targeting the n8n workflow automation platform to steal developers’ OAuth credentials. One such package, named “n8n-nodes-hfgjf-irtuinvcm-lasdqewriit,” mimics a Google Ads integration, and prompts users to link their advertising account in a seemingly legitimate form and then … Read More “n8n Supply Chain Attack Abuses Community Nodes to Steal OAuth Tokens – The Hacker News” »
Researchers at Palo Alto’s Unit 42 have outlined a list of recommended security controls for vibe coding tools – Read More –
Everest Ransomware Claims Breach at Nissan, Says 900GB of Data Stolen – Hackread – Cybersecurity News, Data Breaches, AI, and More

Everest ransomware claims to have breached Nissan Motor Corporation, alleging the theft of 900GB of internal data, including documents and screenshots. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Cybersecurity in the Public Sector: Challenges, Strategies and Best Practices – Hackread – Cybersecurity News, Data Breaches, AI, and More

Public sector cybersecurity faces outdated systems, budget gaps, and rising attacks. Learn key challenges, defense strategies, and proven best practices. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
US agency CISA has retired ten Emergency Directives issued between 2019 and 2024, marking a new step in managing federal cyber-risk – Read More –
As we ramp up to the premier automotive and charging station hacking competition, Pwn2Own Automotive 2026 in Tokyo, the Trend Micro Zero Day Initiative (ZDI) is providing a preliminary look at one of the main targets: the Alpitronic HYC50 High-Power Charger. The HYC50 series represents the leading edge of fast-charging infrastructure, blending complex high-voltage power … Read More “The Alpitronic HYC50 Hardware Teardown for Pwn2Own Automotive 2026 – Zero Day Initiative – Blog” »
California privacy regulator, the CPPA, is cracking down on data brokers trading personal data without authorization – Read More –
World Economic Forum: Cyber-fraud overtakes ransomware as business leaders’ top cyber-security concern –

“Pervasive” threat of phishing, invoice scams and other cyber-enabled fraud is at “record highs”, warns WEF Cybersecurity Outlook 2026 – Read More –
This week made one thing clear: small oversights can spiral fast. Tools meant to save time and reduce friction turned into easy entry points once basic safeguards were ignored. Attackers didn’t need novel tricks. They used what was already exposed and moved in without resistance. Scale amplified the damage. A single weak configuration rippled out … Read More “⚡ Weekly Recap: AI Automation Exploits, Telecom Espionage, Prompt Poaching & More – The Hacker News” »
GoBruteforcer Botnet Targets Crypto Project Databases by Exploiting Weak Credentials – The Hacker News
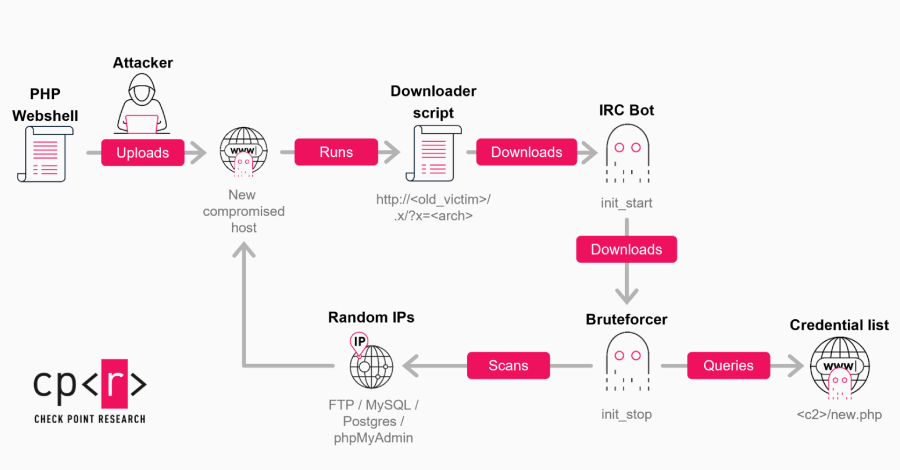
A new wave of GoBruteforcer attacks has targeted databases of cryptocurrency and blockchain projects to co-opt them into a botnet that’s capable of brute-forcing user passwords for services such as FTP, MySQL, PostgreSQL, and phpMyAdmin on Linux servers. “The current wave of campaigns is driven by two factors: the mass reuse of AI-generated server deployment … Read More “GoBruteforcer Botnet Targets Crypto Project Databases by Exploiting Weak Credentials – The Hacker News” »









![[Webinar] Securing Agentic AI: From MCPs and Tool Access to Shadow API Key Sprawl – The Hacker News](https://attackfeed.com/wp-content/uploads/2026/01/ai-agent-C3Hsu0.webp)