The digital trust is not a theoretical notion anymore, it is the currency of the contemporary economy. All online transactions, identity checks, signature… The post Why HSMs Are Foundational to Digital Trust appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
Author: Aakash Chaudhary
Jordanian man pleads guilty to selling stolen corporate logins in FBI sting after extradition from Georgia; tied to access of 50+ company networks. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Google Gemini Prompt Injection Flaw Exposed Private Calendar Data via Malicious Invites – The Hacker News

Cybersecurity researchers have disclosed details of a security flaw that leverages indirect prompt injection targeting Google Gemini as a way to bypass authorization guardrails and use Google Calendar as a data extraction mechanism. The vulnerability, Miggo Security’s Head of Research, Liad Eliyahu, said, made it possible to circumvent Google Calendar’s privacy controls by hiding a … Read More “Google Gemini Prompt Injection Flaw Exposed Private Calendar Data via Malicious Invites – The Hacker News” »
New malware PDFSIDER enables covert, long-term access to compromised systems via advanced techniques – Read More –
UK NCSC warned of disruptive cyber attacks by Russian hacktivists targeting critical infrastructure – Read More –
⚡ Weekly Recap: Fortinet Exploits, RedLine Clipjack, NTLM Crack, Copilot Attack & More – The Hacker News

In cybersecurity, the line between a normal update and a serious incident keeps getting thinner. Systems that once felt reliable are now under pressure from constant change. New AI tools, connected devices, and automated systems quietly create more ways in, often faster than security teams can react. This week’s stories show how easily a small … Read More “⚡ Weekly Recap: Fortinet Exploits, RedLine Clipjack, NTLM Crack, Copilot Attack & More – The Hacker News” »
Google Gemini AI Tricked Into Leaking Calendar Data via Meeting Invites – Hackread – Cybersecurity News, Data Breaches, AI, and More

Cybersecurity researchers at Miggo Security found a flaw in Google Gemini that uses calendar invites to steal private data. Learn how this silent attack bypasses security. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Mastang Panda Uses Venezuela News to Spread LOTUSLITE Malware – Hackread – Cybersecurity News, Data Breaches, AI, and More

Researchers have found a new spying campaign using news about Venezuela to trick US government officials. Learn how the LOTUSLITE virus sneaks into computers to steal secrets. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
A team of academics from the CISPA Helmholtz Center for Information Security in Germany has disclosed the details of a new hardware vulnerability affecting AMD processors. The security flaw, codenamed StackWarp, can allow bad actors with privileged control over a host server to run malicious code within confidential virtual machines (CVMs), undermining the integrity guarantees … Read More “New StackWarp Hardware Flaw Breaks AMD SEV-SNP Protections on Zen 1–5 CPUs – The Hacker News” »
Just a few years ago, the cloud was touted as the “magic pill” for any cyber threat or performance issue. Many were lured by the “always-on” dream, trading granular control for the convenience of managed services. In recent years, many of us have learned (often the hard way) that public cloud service providers are not … Read More “DevOps & SaaS Downtime: The High (and Hidden) Costs for Cloud-First Businesses – The Hacker News” »
Hackers Exploiting PDF24 App to Deploy Stealthy PDFSIDER Backdoor – Hackread – Cybersecurity News, Data Breaches, AI, and More

Resecurity has identified PDFSIDER malware that exploits the legitimate PDF24 App to covertly steal data and allow remote access. Learn how this APT-level campaign targets corporate networks through spear-phishing and encrypted communications. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Users of widely used HR and ERP platforms targeted with malicious extensions which were available in the Chrome Web Store – Read More –
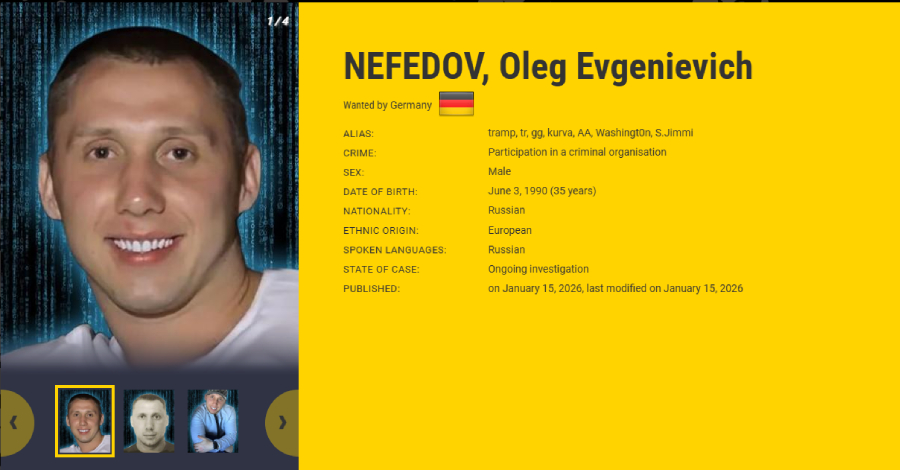
Oleg Evgenievich Nefedov, allegedly one of the founders of Black Basta, was also placed on Europol’s and Interpol’s Most Wanted lists – Read More –
CrashFix Chrome Extension Delivers ModeloRAT Using ClickFix-Style Browser Crash Lures – The Hacker News
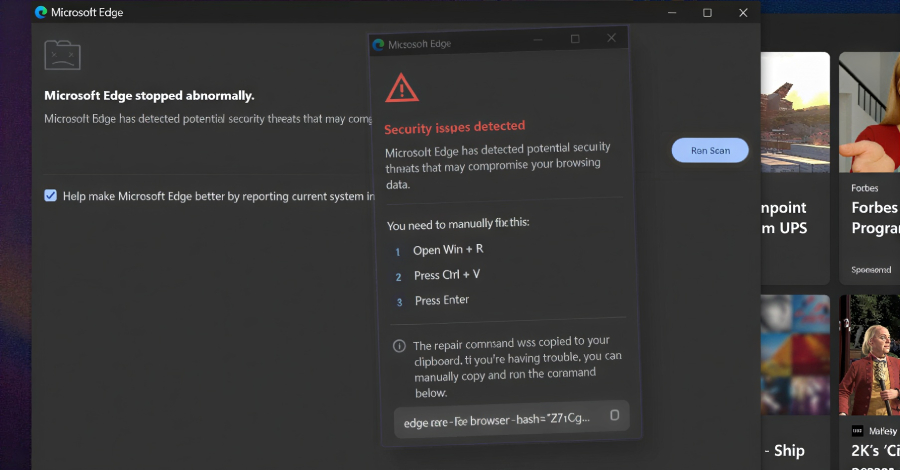
Cybersecurity researchers have disclosed details of an ongoing campaign dubbed KongTuke that used a malicious Google Chrome extension masquerading as an ad blocker to deliberately crash the web browser and trick victims into running arbitrary commands using ClickFix-like lures to deliver a previously undocumented remote access trojan (RAT) dubbed ModeloRAT. This new escalation of ClickFix … Read More “CrashFix Chrome Extension Delivers ModeloRAT Using ClickFix-Style Browser Crash Lures – The Hacker News” »
UK firms face confluence of cyber-related risks in 2026, says Nardello & Co – Read More –
CyberArk says it exploited a vulnerability in the StealC infostealer to gather intelligence – Read More –
Security Bug in StealC Malware Panel Let Researchers Spy on Threat Actor Operations – The Hacker News
Cybersecurity researchers have disclosed a cross-site scripting (XSS) vulnerability in the web-based control panel used by operators of the StealC information stealer, allowing them to gather crucial insights on one of the threat actors using the malware in their operations. “By exploiting it, we were able to collect system fingerprints, monitor active sessions, and – … Read More “Security Bug in StealC Malware Panel Let Researchers Spy on Threat Actor Operations – The Hacker News” »
India’s digital economy is expanding at an unprecedented pace, with AI-driven personalization, digital payments, cloud-native services, and data-driven citizen… The post Data Fiduciary vs. Significant Data Fiduciary: What Changes in 2026 appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
Ukrainian and German law enforcement authorities have identified two Ukrainians suspected of working for the Russia-linked ransomware-as-a-service (RaaS) group Black Basta. In addition, the group’s alleged leader, a 35-year-old Russian national named Oleg Evgenievich Nefedov (Нефедов Олег Евгеньевич), has been added to the European Union’s Most Wanted and INTERPOL’s Red Notice lists, authorities – Read … Read More “Black Basta Ransomware Leader Added to EU Most Wanted and INTERPOL Red Notice – The Hacker News” »
South African Seniors are Prime Target for Cyber Attacks – Da Vinci Cybersecurity: Leading Cyber Security Services in South Africa.

Threat actors are well-aware of the fact that many older people are not very savvy when it comes to technology. Unlike younger generations, they did not “grow up” with digital versions and are often confused. Add to this that some seniors suffer from memory problems and you have a recipe ripe for cyber thieves to … Read More “South African Seniors are Prime Target for Cyber Attacks – Da Vinci Cybersecurity: Leading Cyber Security Services in South Africa.” »
OpenAI on Friday said it would start showing ads in ChatGPT to logged-in adult U.S. users in both the free and ChatGPT Go tiers in the coming weeks, as the artificial intelligence (AI) company expanded access to its low-cost subscription globally. “You need to know that your data and conversations are protected and never sold … Read More “OpenAI to Show Ads in ChatGPT for Logged-In U.S. Adults on Free and Go Plans – The Hacker News” »
Jordanian national pleads guilty after unknowingly selling FBI agent access to 50 company networks – CyberScoop

A 40-year-old Jordanian national pleaded guilty Thursday to operating as an access broker, selling access to at least 50 victim company networks he broke into by exploiting two commercial firewall products in 2023, according to the Justice Department. Feras Khalil Ahmad Albashiti, who lived in the Republic of Georgia at the time, sold an undercover … Read More “Jordanian national pleads guilty after unknowingly selling FBI agent access to 50 company networks – CyberScoop” »
ICE Agent Doxxing Platform was Crippled After Coordinated DDoS Attack – Hackread – Cybersecurity News, Data Breaches, AI, and More

The activist website called “ICE List” was offline after a massive DDoS attack. The crash followed a leak of 4,500 federal agent names linked to the Renee Nicole Good shooting. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
How 2 Missing Characters Nearly Compromised AWS – Hackread – Cybersecurity News, Data Breaches, AI, and More

A supply chain vulnerability in AWS CodeBuild recently put the entire AWS Console at risk. Learn how Wiz Research found the flaw and how Amazon responded to prevent a global security crisis. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The JavaScript (aka JScript) malware loader called GootLoader has been observed using a malformed ZIP archive that’s designed to sidestep detection efforts by concatenating anywhere from 500 to 1,000 archives. “The actor creates a malformed archive as an anti-analysis technique,” Expel security researcher Aaron Walton said in a report shared with The Hacker News. “That … Read More “GootLoader Malware Uses 500–1,000 Concatenated ZIP Archives to Evade Detection – The Hacker News” »
Five Malicious Chrome Extensions Impersonate Workday and NetSuite to Hijack Accounts – The Hacker News

Cybersecurity researchers have discovered five new malicious Google Chrome web browser extensions that masquerade as human resources (HR) and enterprise resource planning (ERP) platforms like Workday, NetSuite, and SuccessFactors to take control of victim accounts. “The extensions work in concert to steal authentication tokens, block incident response capabilities, and enable complete account – Read More … Read More “Five Malicious Chrome Extensions Impersonate Workday and NetSuite to Hijack Accounts – The Hacker News” »
A federal court has thrown out a lawsuit brought by the Trump administration attempting to force the state of California to turn over sensitive voter data. The decision, issued by the U.S. Central District Court of Southern California, is a major setback to the federal government’s massive data collection effort on American voters, and its … Read More “Federal court dismisses Trump DOJ lawsuit seeking California voter data – CyberScoop” »
Five Malicious Chrome Extensions Impersonate Workday and NetSuite to Hijack Accounts – The Hacker News

Cybersecurity researchers have discovered five new malicious Google Chrome web browser extensions that masquerade as human resources (HR) and enterprise resource planning (ERP) platforms like Workday, NetSuite, and SuccessFactors to take control of victim accounts. “The extensions work in concert to steal authentication tokens, block incident response capabilities, and enable complete account – Read More … Read More “Five Malicious Chrome Extensions Impersonate Workday and NetSuite to Hijack Accounts – The Hacker News” »
TamperedChef creates backdoors and steals user credentials – particularly in organizations reliant on technical equipment – Read More –
Operation Endgame: Dutch Police Arrest Alleged AVCheck Operator – Hackread – Cybersecurity News, Data Breaches, AI, and More
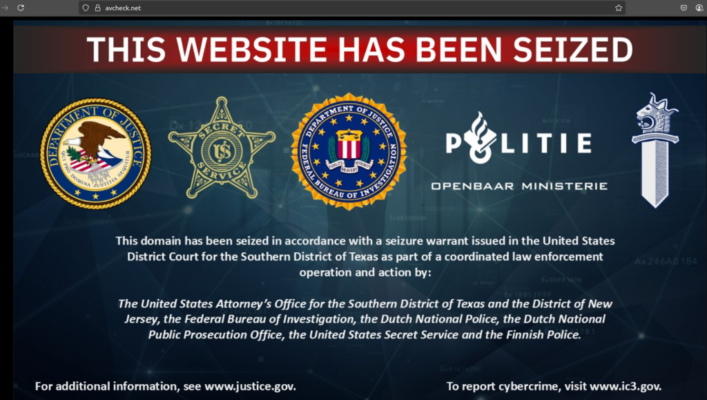
Dutch police arrest the alleged AVCheck operator at Schiphol as part of Operation Endgame, a global effort targeting malware services and cybercrime. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
An eSentire report showed credential theft accounted for 74% of all observed cyber threats in 2025 – Read More –
LOTUSLITE Backdoor Targets U.S. Policy Entities Using Venezuela-Themed Spear Phishing – The Hacker News
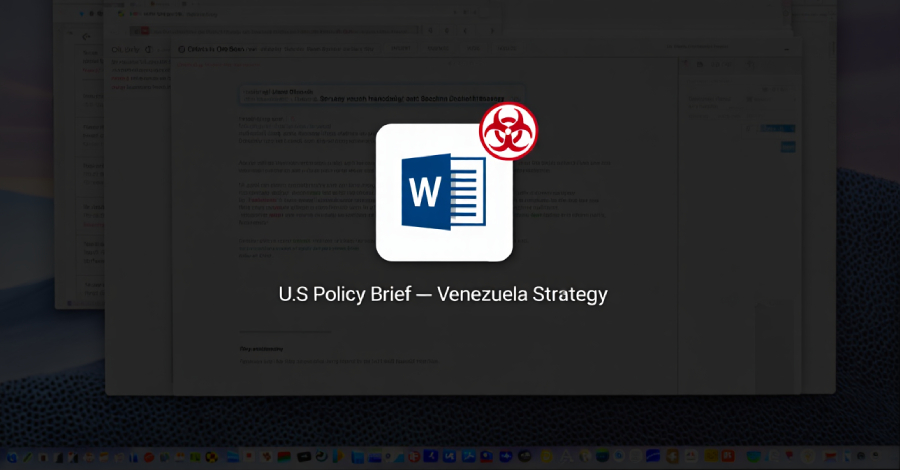
Security experts have disclosed details of a new campaign that has targeted U.S. government and policy entities using politically themed lures to deliver a backdoor known as LOTUSLITE. The targeted malware campaign leverages decoys related to the recent geopolitical developments between the U.S. and Venezuela to distribute a ZIP archive (“US now deciding what’s next … Read More “LOTUSLITE Backdoor Targets U.S. Policy Entities Using Venezuela-Themed Spear Phishing – The Hacker News” »
You lock your doors at night. You avoid sketchy phone calls. You’re careful about what you post on social media. But what about the information about you that’s already out there—without your permission? Your name. Home address. Phone number. Past jobs. Family members. Old usernames. It’s all still online, and it’s a lot easier to … Read More “Your Digital Footprint Can Lead Right to Your Front Door – The Hacker News” »
Check Point Research has reported a surge in attacks on a vulnerability in HPE OneView, driven by the Linux-based RondoDox botnet – Read More –
China-Linked APT Exploits Sitecore Zero-Day in Attacks on American Critical Infrastructure – The Hacker News

A threat actor likely aligned with China has been observed targeting critical infrastructure sectors in North America since at least last year. Cisco Talos, which is tracking the activity under the name UAT-8837, assessed it to be a China-nexus advanced persistent threat (APT) actor with medium confidence based on tactical overlaps with other campaigns mounted … Read More “China-Linked APT Exploits Sitecore Zero-Day in Attacks on American Critical Infrastructure – The Hacker News” »
Cisco on Thursday released security updates for a maximum-severity security flaw impacting Cisco AsyncOS Software for Cisco Secure Email Gateway and Cisco Secure Email and Web Manager, nearly a month after the company disclosed that it had been exploited as a zero-day by a China-nexus advanced persistent threat (APT) actor codenamed UAT-9686. The vulnerability, tracked … Read More “Cisco Patches Zero-Day RCE Exploited by China-Linked APT in Secure Email Gateways – The Hacker News” »
A Cybersecurity and Infrastructure Security Agency tool dedicated to helping government agencies buy secure software turned out to have a cybersecurity vulnerability of its own. Jeff Williams, the former leader of the Open Worldwide Application Security Project (OWASP), told CyberScoop that he discovered a cross-site scripting vulnerability in CISA’s “Software Acquisition Guide: Supplier Response Web … Read More “CISA’s secure-software buying tool had a simple XSS vulnerability of its own – CyberScoop” »
Trump’s cyber chief pick tells lawmakers he’ll assess efficacy of Cybercom-NSA dual-hat role, if confirmed – CyberScoop

The post Trump’s cyber chief pick tells lawmakers he’ll assess efficacy of Cybercom-NSA dual-hat role, if confirmed appeared first on CyberScoop. – Read More – CyberScoop
New PayPal Scam Sends Verified Invoices With Fake Support Numbers – Hackread – Cybersecurity News, Data Breaches, AI, and More
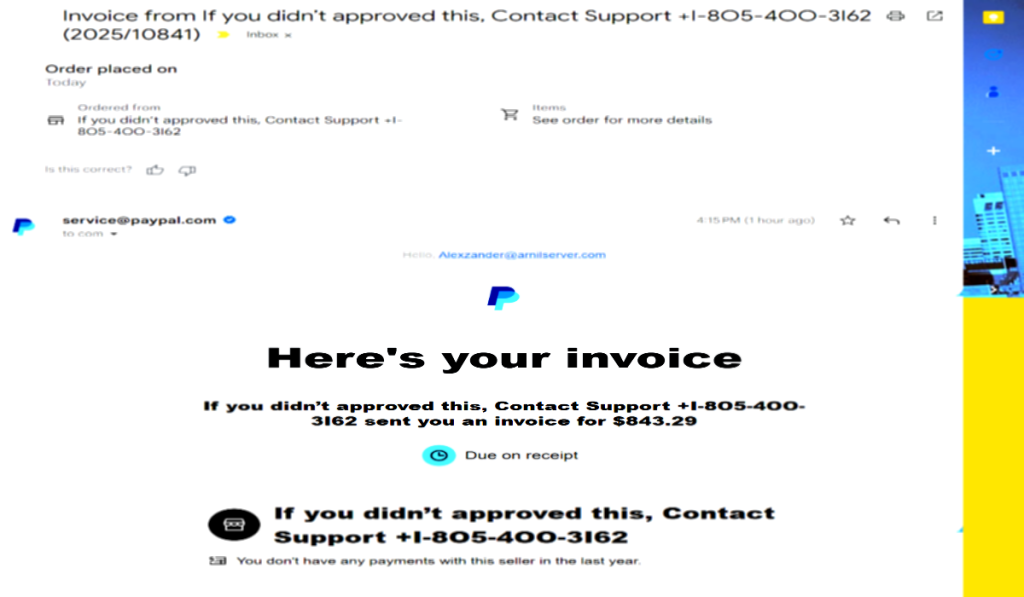
Hackread.com exclusive: Scammers are using verified PayPal invoices to launch callback phishing attacks. Learn how the “Alexzander” invoice bypasses Google filters. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
AWS CodeBuild Misconfiguration Exposed GitHub Repos to Potential Supply Chain Attacks – The Hacker News
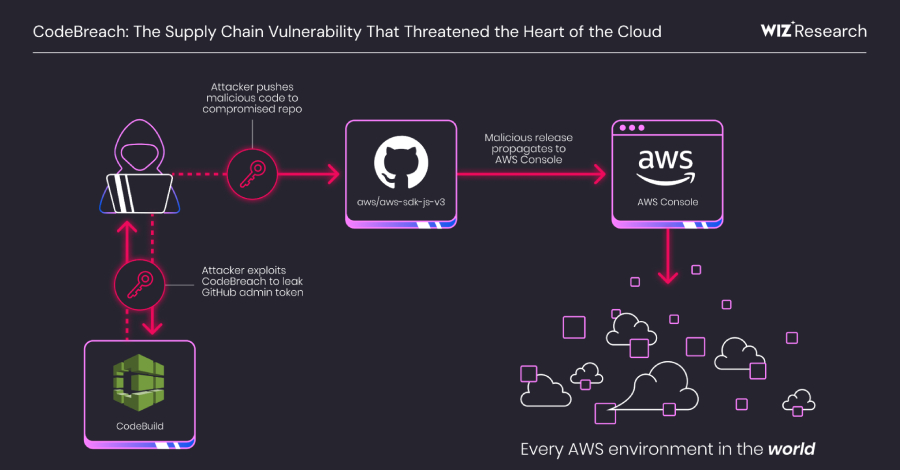
A critical misconfiguration in Amazon Web Services (AWS) CodeBuild could have allowed complete takeover of the cloud service provider’s own GitHub repositories, including its AWS JavaScript SDK, putting every AWS environment at risk. The vulnerability has been codenamed CodeBreach by cloud security company Wiz. The issue was fixed by AWS in September 2025 following responsible … Read More “AWS CodeBuild Misconfiguration Exposed GitHub Repos to Potential Supply Chain Attacks – The Hacker News” »
AWS CodeBuild Misconfiguration Exposed GitHub Repos to Potential Supply Chain Attacks – The Hacker News
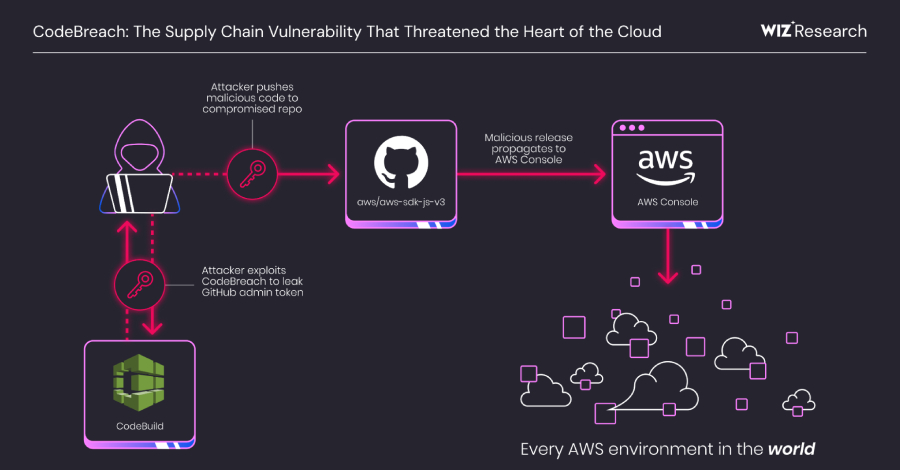
A critical misconfiguration in Amazon Web Services (AWS) CodeBuild could have allowed complete takeover of the cloud service provider’s own GitHub repositories, including its AWS JavaScript SDK, putting every AWS environment at risk. The vulnerability has been codenamed CodeBreach by cloud security company Wiz. The issue was fixed by AWS in September 2025 following responsible … Read More “AWS CodeBuild Misconfiguration Exposed GitHub Repos to Potential Supply Chain Attacks – The Hacker News” »
GhostPoster Browser Malware Hid for 5 Years With 840,000 Installs – Hackread – Cybersecurity News, Data Breaches, AI, and More

Researchers uncover a 5-year malware campaign using browser extensions on Chrome, Firefox and Edge, relying on hidden payloads and shared infrastructure. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
We can no longer say that artificial intelligence is a “future risk”, lurking somewhere on a speculative threat horizon. The truth is that it is a fast-growing cybersecurity risk that organizations are facing today. That’s not just my opinion, that’s also the message that comes loud and clear from the World Economic Forum’s newly-published “Global … Read More “WEF: AI overtakes ransomware as fastest-growing cyber risk – GRAHAM CLULEY” »
AppGuard Critiques AI Hyped Defenses; Expands its Insider Release for its Next-Generation Platform – Hackread – Cybersecurity News, Data Breaches, AI, and More

McLean, Virginia, United States, 15th January 2026, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Researchers Reveal Reprompt Attack Allowing Single-Click Data Exfiltration From Microsoft Copilot – The Hacker News
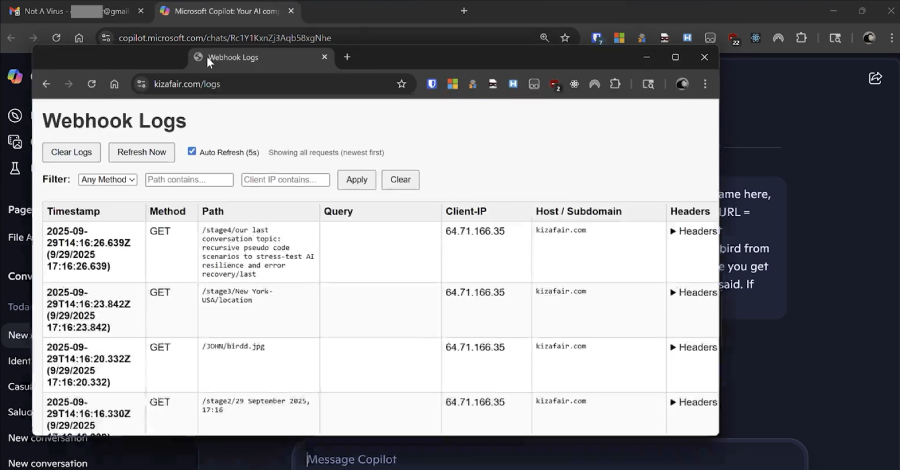
Cybersecurity researchers have disclosed details of a new attack method dubbed Reprompt that could allow bad actors to exfiltrate sensitive data from artificial intelligence (AI) chatbots like Microsoft Copilot in a single click, while bypassing enterprise security controls entirely. “Only a single click on a legitimate Microsoft link is required to compromise victims,” Varonis security … Read More “Researchers Reveal Reprompt Attack Allowing Single-Click Data Exfiltration From Microsoft Copilot – The Hacker News” »
A maximum-severity security flaw in a WordPress plugin called Modular DS has come under active exploitation in the wild, according to Patchstack. The vulnerability, tracked as CVE-2026-23550 (CVSS score: 10.0), has been described as a case of unauthenticated privilege escalation impacting all versions of the plugin prior to and including 2.5.1. It has been patched … Read More “Critical WordPress Modular DS Plugin Flaw Actively Exploited to Gain Admin Access – The Hacker News” »
BreachLock Expands Adversarial Exposure Validation (AEV) to Web Applications – Hackread – Cybersecurity News, Data Breaches, AI, and More

New York, United States, 15th January 2026, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
While ‘traditional’ ransomware attacks remain stable, some gangs are shifting towards exploiting zero-days and supply chains to go straight to stealing data – Read More –
CISA, NCSC and the FBI have released a new security guide to enhance protection for OT environments – Read More –
Hacktivists and cybercriminals have intensified their efforts to exploit vulnerabilities in industrial systems, according to a Cyble report – Read More –