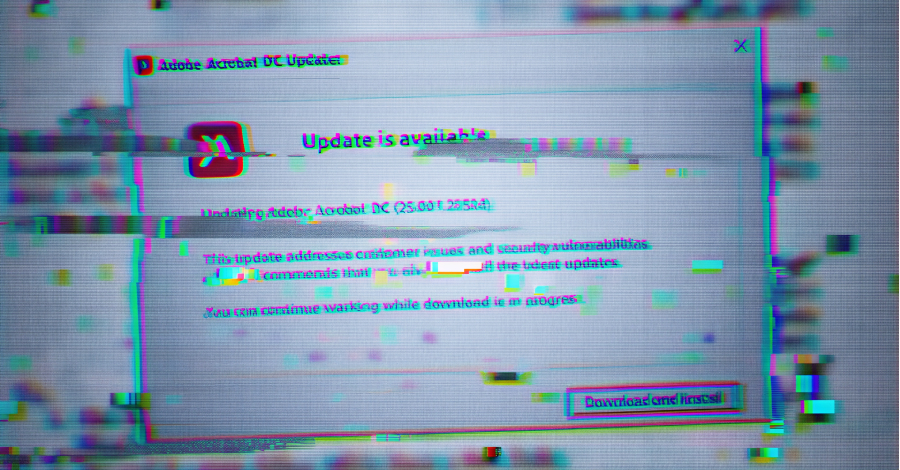
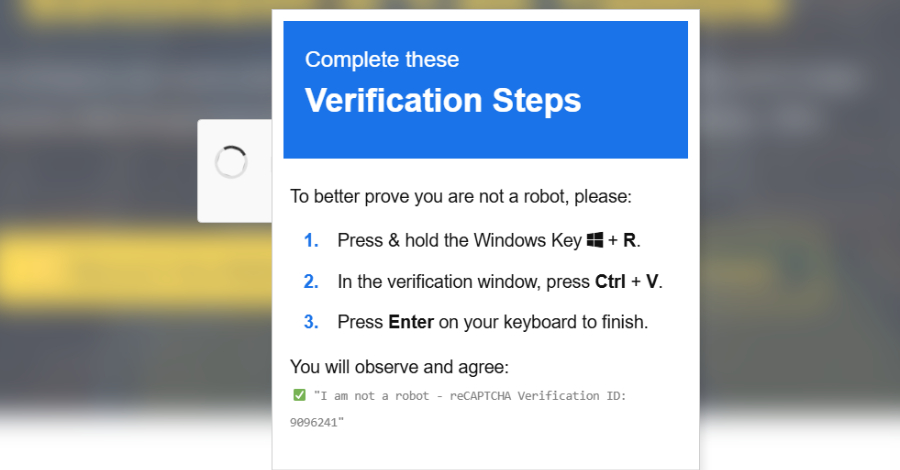
16 Fake ChatGPT Extensions Caught Hijacking User Accounts – Hackread – Cybersecurity News, Data Breaches, AI, and More

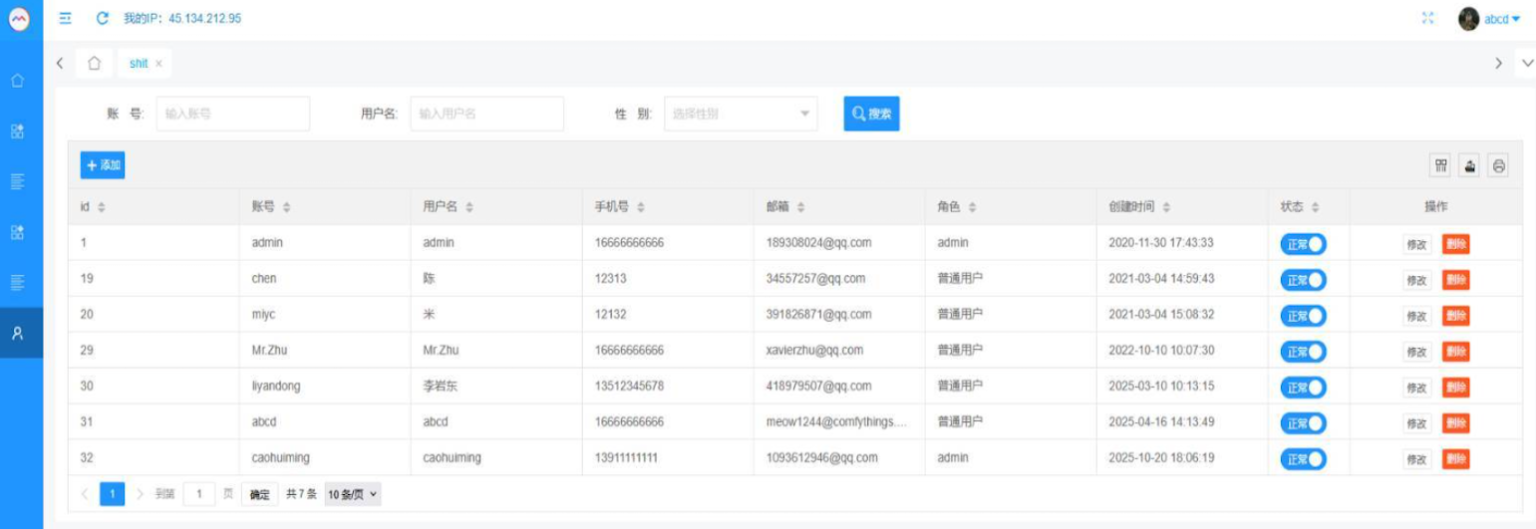
A coordinated campaign of 16 malicious GPT optimisers has been caught hijacking ChatGPT accounts. These tools steal session tokens to access private chats, Slack, and Google Drive files. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More