Google has taken coordinated action against the massive IPIDEA residential proxy network, enhancing customer protections and disrupting cybercrime operations – Read More –
Author: Joe-W
CISA urges action against insider threats with publication of a new infographic offering strategies to manage risks – Read More –
This startup aims to solve crypto’s broken key management problem – Hackread – Cybersecurity News, Data Breaches, AI, and More

Crypto security firm Sodot launches Exchange API Vault to stop API key theft, securing billions in assets while supporting low latency, high frequency trading. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Malicious Google Ads Target Mac Users with Fake Mac Cleaner Pages – Hackread – Cybersecurity News, Data Breaches, AI, and More
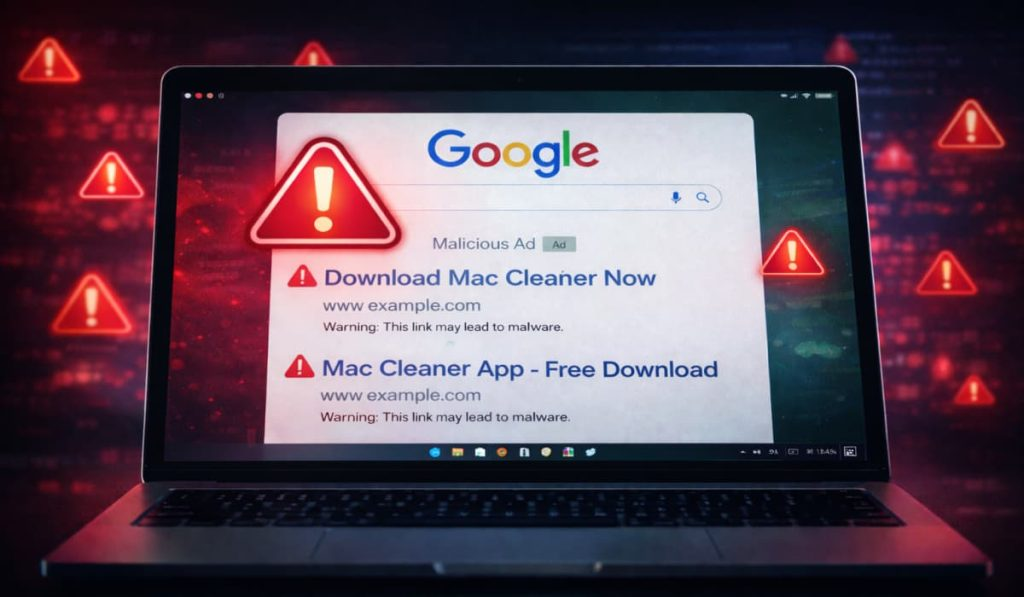
Mac users searching for software on Google or other search engines should be extra careful. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
US Sentences Chinese National for Role in $36.9 Million Crypto Scam – Hackread – Cybersecurity News, Data Breaches, AI, and More

A Chinese national has been sentenced for his role in a massive $36.9 million cryptocurrency scam operated from… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
This week’s updates show how small changes can create real problems. Not loud incidents, but quiet shifts that are easy to miss until they add up. The kind that affects systems people rely on every day. Many of the stories point to the same trend: familiar tools being used in unexpected ways. Security controls are … Read More “ThreatsDay Bulletin: New RCEs, Darknet Busts, Kernel Bugs & 25+ More Stories – The Hacker News” »
The dark web forum administrator confirmed the takedown and said they had “no plans to rebuild” – Read More –
A study by OMICRON has revealed widespread cybersecurity gaps in the operational technology (OT) networks of substations, power plants, and control centers worldwide. Drawing on data from more than 100 installations, the analysis highlights recurring technical, organizational, and functional issues that leave critical energy infrastructure vulnerable to cyber threats. The findings are based on – … Read More “Survey of 100+ Energy Systems Reveals Critical OT Cybersecurity Gaps – The Hacker News” »
Beyond the direct impact of cyberattacks, enterprises suffer from a secondary but potentially even more costly risk: operational downtime, any amount of which translates into very real damage. That’s why for CISOs, it’s key to prioritize decisions that reduce dwell time and protect their company from risk. Three strategic steps you can take this year … Read More “3 Decisions CISOs Need to Make to Prevent Downtime Risk in 2026 – The Hacker News” »
A North Korea-backed threat group operating since 2009 has splintered into three distinct groups with specialized malware and objectives, CrowdStrike said in a report released Thursday. Labeled “Labyrinth Chollima” by the company, the group follows a divergence pattern CrowdStrike observed previously. Labyrinth Chollima has spawned two additional groups: Golden Chollima and Pressure Chollima. The spin-offs, … Read More “Long-running North Korea threat group splits into 3 distinct operations – CyberScoop” »
SolarWinds Fixes Four Critical Web Help Desk Flaws With Unauthenticated RCE and Auth Bypass – The Hacker News

SolarWinds has released security updates to address multiple security vulnerabilities impacting SolarWinds Web Help Desk, including four critical vulnerabilities that could result in authentication bypass and remote code execution (RCE). The list of vulnerabilities is as follows – CVE-2025-40536 (CVSS score: 8.1) – A security control bypass vulnerability that could allow an unauthenticated – Read … Read More “SolarWinds Fixes Four Critical Web Help Desk Flaws With Unauthenticated RCE and Auth Bypass – The Hacker News” »
Despite the seemingly widespread adoption of AI for security operations, security leaders primarily use it for “relatively basic use cases,” said a Sumo Logic study – Read More –
Cybersecurity is now the fifth fastest-growing occupation in the UK, says Socura – Read More –
One small step for Cyber Resilience Test Facilities, one giant leap for technology assurance – NCSC Feed

CRTFs are helping organisations to make informed, risk-based decisions on the adoption of technology products. – Read More – NCSC Feed
Google on Wednesday announced that it worked together with other partners to disrupt IPIDEA, which it described as one of the largest residential proxy networks in the world. To that end, the company said it took legal action to take down dozens of domains used to control devices and proxy traffic through them. As of … Read More “Google Disrupts IPIDEA — One of the World’s Largest Residential Proxy Networks – The Hacker News” »
In a period characterized by the acceleration of digital faster, more regulatory bodies and constant cyber threats, data protection… The post Designing an End-to-End Data Protection Architecture appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
Smashing Security podcast #452: The dark web’s worst assassins, and Pegasus in the dock – GRAHAM CLULEY

In episode 452, a London-based YouTuber wins a landmark court case against Saudi Arabia after his phone was hacked with Pegasus spyware — exposing how a single, seemingly harmless text message can turn a smartphone into a round-the-clock surveillance device. Plus, we go looking for professional hitmen online – only to uncover uncomfortable questions about … Read More “Smashing Security podcast #452: The dark web’s worst assassins, and Pegasus in the dock – GRAHAM CLULEY” »
Lawmakers wonder when Trump administration will weigh on soon-expired surveillance powers – CyberScoop

There’s a growing question on Capitol Hill as the expiration of sweeping U.S. government surveillance powers looms: Where is the Trump administration? The Senate Judiciary Committee held a hearing Wednesday on the 2024 law that revised the surveillance authorities known as Section 702, a part of the Foreign Intelligence Surveillance Act. Advocates have said that … Read More “Lawmakers wonder when Trump administration will weigh on soon-expired surveillance powers – CyberScoop” »
Fortinet’s latest zero-day vulnerability carries frustrating familiarities for customers – CyberScoop

Fortinet customers are confronting another actively exploited zero-day vulnerability that allows attackers to bypass authentication in the single sign-on flow for FortiCloud and gain privileged access to multiple Fortinet firewall products and related services. The vendor issued a security advisory for the vulnerability — CVE-2026-24858 — warning that some instances of exploitation already occurred earlier … Read More “Fortinet’s latest zero-day vulnerability carries frustrating familiarities for customers – CyberScoop” »
A class of individuals who say they were victimized by nude or undressed deepfakes generated by Grok have filed a lawsuit against parent company xAI, calling the tool “a generative artificial intelligence chatbot that humiliates and sexually exploits women and girls by undressing them and posing them in sexual positions in deepfake images publicly posted … Read More “Undressed victims file class action lawsuit against xAI for Grok deepfakes – CyberScoop” »
How badly do you want to win an online argument? I certainly hope it’s not enough to put the life of the other person at risk. Police in Hungary and Romania have arrested four young men suspected of making hoax bomb threats and terrorising internet users through SWATting and doxing attacks. Read more in my … Read More “Four arrested in crackdown on Discord-based SWATting and doxing – GRAHAM CLULEY” »
Why RAMS Software Is Becoming Essential for Construction Safety and Compliance – Hackread – Cybersecurity News, Data Breaches, AI, and More

Digital RAMS software helps construction teams manage risk assessments, method statements, and safety compliance across sites with real-time access. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Burner phones and lead-lined bags: a history of UK security tactics in China – Data and computer security | The Guardian

Starmer’s team is wary of spies but such fears are not new – with Theresa May once warned to get dressed under a duvet When prime ministers travel to China, heightened security arrangements are a given – as is the quiet game of cat and mouse that takes place behind the scenes as each country … Read More “Burner phones and lead-lined bags: a history of UK security tactics in China – Data and computer security | The Guardian” »
Hackers Still Using Patched WinRAR Flaw for Malware Drops, Warns Google – Hackread – Cybersecurity News, Data Breaches, AI, and More
The Google Threat Intelligence Group (GTIG) warns that nation-state actors and financially motivated threat actors are exploiting a… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The “coordinated” cyber attack targeting multiple sites across the Polish power grid has been attributed with medium confidence to a Russian state-sponsored hacking crew known as ELECTRUM. Operational technology (OT) cybersecurity company Dragos, in a new intelligence brief published Tuesday, described the late December 2025 activity as the first major cyber attack targeting distributed energy … Read More “Russian ELECTRUM Tied to December 2025 Cyber Attack on Polish Power Grid – The Hacker News” »
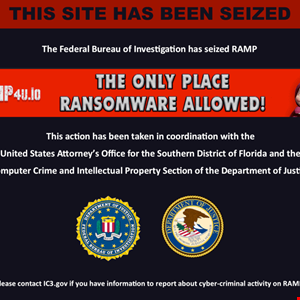
Russian Cybercrime Platform RAMP Forum Seized by FBI – Hackread – Cybersecurity News, Data Breaches, AI, and More
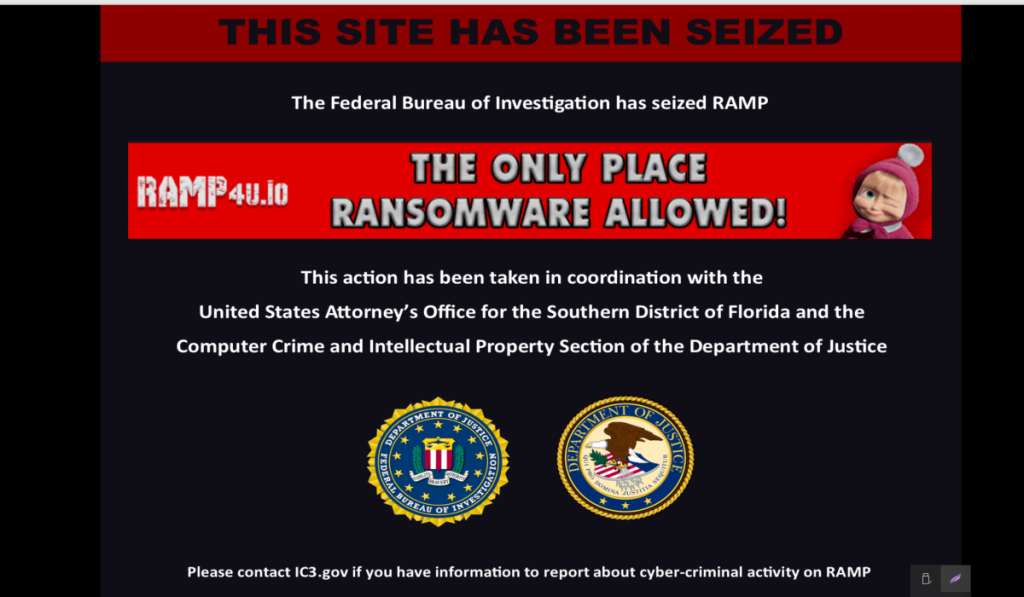
US authorities have seized the RAMP cybercrime forum, taking down both its clearnet and dark web domains in a major hit to the ransomware infrastructure. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Cybersecurity researchers have flagged a new malicious Microsoft Visual Studio Code (VS Code) extension for Moltbot (formerly Clawdbot) on the official Extension Marketplace that claims to be a free artificial intelligence (AI) coding assistant, but stealthily drops a malicious payload on compromised hosts. The extension, named “ClawdBot Agent – AI Coding Assistant” (“clawdbot.clawdbot-agent”) – Read … Read More “Fake Moltbot AI Coding Assistant on VS Code Marketplace Drops Malware – The Hacker News” »
A recent update has fixed 12 vulnerabilities in OpenSSL, some existing in the codebase for years – Read More –
Two critical security flaws in n8n have exposed sandboxing vulnerabilities, enabling remote code execution for attackers – Read More –
A critical sandbox escape vulnerability has been disclosed in the popular vm2 Node.js library that, if successfully exploited, could allow attackers to run arbitrary code on the underlying operating system. The vulnerability, tracked as CVE-2026-22709, carries a CVSS score of 9.8 out of 10.0 on the CVSS scoring system. “In vm2 for version 3.10.0, Promise.prototype.then … Read More “Critical vm2 Node.js Flaw Allows Sandbox Escape and Arbitrary Code Execution – The Hacker News” »
Multiple vulnerabilities have been discovered in SolarWinds Web Help Desk, the most severe of which could allow for arbitrary code execution. SolarWinds Web Help Desk (WHD) is a web-based software that provides IT help desk and asset management functionality, allowing IT teams to manage service requests, track IT assets, and offer self-service options to end-users. … Read More “Multiple Vulnerabilities in SolarWinds Web Help Desk Could Allow for Arbitrary Code Execution – Cyber Security Advisories – MS-ISAC” »
Threat actors with ties to China have been observed using an updated version of a backdoor called COOLCLIENT in cyber espionage attacks in 2025 to facilitate comprehensive data theft from infected endpoints. The activity has been attributed to Mustang Panda (aka Earth Preta, Fireant, HoneyMyte, Polaris, and Twill Typhoon) with the intrusions primarily directed against … Read More “Mustang Panda Deploys Updated COOLCLIENT Backdoor in Government Cyber Attacks – The Hacker News” »
If you work in security operations, the concept of the AI SOC agent is likely familiar. Early narratives promised total autonomy. Vendors seized on the idea of the “Autonomous SOC” and suggested a future where algorithms replaced analysts. That future has not arrived. We have not seen mass layoffs or empty security operations centers. We … Read More “From Triage to Threat Hunts: How AI Accelerates SecOps – The Hacker News” »
Cybersecurity researchers have disclosed two new security flaws in the n8n workflow automation platform, including a crucial vulnerability that could result in remote code execution. The weaknesses, discovered by the JFrog Security Research team, are listed below – CVE-2026-1470 (CVSS score: 9.9) – An eval injection vulnerability that could allow an authenticated user to bypass … Read More “Two High-Severity n8n Flaws Allow Authenticated Remote Code Execution – The Hacker News” »
GoTo Resolve Tool’s Background Activities Compared to Ransomware Tactics – Hackread – Cybersecurity News, Data Breaches, AI, and More

New research from Point Wild’s Lat61 team reveals how the HEURRemoteAdmin.GoToResolve.gen tool allows silent, unattended access to PCs. Learn why this legitimate remote administration software is being flagged as a security risk and its surprising connection to ransomware tactics. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Researchers discover that PureRAT’s code now contains emojis – indicating it has been written by AI based-on comments ripped from social media. – Read More –
Phantom Malware in Android Game Mods Hijacks Devices for Ad Fraud – Hackread – Cybersecurity News, Data Breaches, AI, and More

Another day, another Android malware strain. This time, Phantom malware (aka Android.Phantom) is targeting users who install third-party gaming apps from unofficial sources. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Best IT Managed Services for Large Enterprises – Hackread – Cybersecurity News, Data Breaches, AI, and More

Learn what defines top-tier enterprise managed IT services, why they matter, and how Mindcore Technologies meets large-scale business demands. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Zscaler analysts found critical vulnerabilities in 100% of enterprise AI systems, with 90% compromised in under 90 minutes – Read More –
A recent Forbes investigation revealed that Microsoft has allegedly been handing over Bitlocker encryption recovery keys to law enforcement when served with warrants. Microsoft says it receives about 20 such requests annually. Taken narrowly, this may appear to be a routine case of lawful compliance. On closer inspection, it raises a consequential question about how … Read More “If you don’t control your keys, you don’t control your data – CyberScoop” »
Chainalysis claims Chinese money launderers now account for 20% of global activity – Read More –
Sonatype warns that open source threats became industrialized with a surge in malicious packages in 2025 – Read More –
Cybersecurity researchers have discovered two malicious packages in the Python Package Index (PyPI) repository that masquerade as spellcheckers but contain functionality to deliver a remote access trojan (RAT). The packages, named spellcheckerpy and spellcheckpy, are no longer available for download, but not before they were collectively downloaded a little over 1,000 times. “Hidden inside the … Read More “Fake Python Spellchecker Packages on PyPI Delivered Hidden Remote Access Trojan – The Hacker News” »
Google on Tuesday revealed that multiple threat actors, including nation-state adversaries and financially motivated groups, are exploiting a now-patched critical security flaw in RARLAB WinRAR to establish initial access and deploy a diverse array of payloads. “Discovered and patched in July 2025, government-backed threat actors linked to Russia and China as well as financially motivated … Read More “Google Warns of Active Exploitation of WinRAR Vulnerability CVE-2025-8088 – The Hacker News” »
When security teams discuss credential-related risk, the focus typically falls on threats such as phishing, malware, or ransomware. These attack methods continue to evolve and rightly command attention. However, one of the most persistent and underestimated risks to organizational security remains far more ordinary. Near-identical password reuse continues to slip past security controls, often – … Read More “Password Reuse in Disguise: An Often-Missed Risky Workaround – The Hacker News” »
If you’ve installed a browser extension to enhance your ChatGPT experience, you might want to think again. Read more in my article on the Hot for Security blog. – Read More – GRAHAM CLULEY
Fortinet has begun releasing security updates to address a critical flaw impacting FortiOS that has come under active exploitation in the wild. The vulnerability, assigned the CVE identifier CVE-2026-24858 (CVSS score: 9.4), has been described as an authentication bypass related to FortiOS single sign-on (SSO). The flaw also affects FortiManager and FortiAnalyzer. The company said … Read More “Fortinet Patches CVE-2026-24858 After Active FortiOS SSO Exploitation Detected – The Hacker News” »
A vulnerability has been discovered in Microsoft Office which could allow for a security feature bypass. Microsoft Office is a suite of applications designed to help with productivity and completing common tasks on a computer. You can create and edit documents containing text and images, work with data in spreadsheets and databases, and create presentations … Read More “A Vulnerability in Microsoft Office Could Allow for Security Feature Bypass – Cyber Security Advisories – MS-ISAC” »
Google Threat Intelligence Group warned that a diverse and growing collection of attackers, including nation-state groups and financially motivated cybercriminals, are exploiting a path-traversal vulnerability affecting WinRAR that was disclosed and patched six months ago. The high-severity vulnerability — CVE-2025-8088 — was exploited in the wild almost two weeks before RARLAB, the vendor behind the … Read More “Cybercriminals and nation-state groups are exploiting a six-month old WinRAR defect – CyberScoop” »
ShinyHunters Target 100+ Firms Using Phone Calls to Bypass SSO Security – Hackread – Cybersecurity News, Data Breaches, AI, and More

ShinyHunters is driving attacks on 100+ organisations, using vishing and fake login pages with allied groups to bypass SSO and steal company data, reports Silent Push. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More