For mid-market organizations, cybersecurity is a constant balancing act. Proactive, preventative security measures are essential to protect an expanding attack surface. Combined with effective protection that blocks threats, they play a critical role in stopping cyberattacks before damage is done. The challenge is that many security tools add complexity and cost that most mid-market businesses … Read More “Securing the Mid-Market Across the Complete Threat Lifecycle – The Hacker News” »
Author: [email protected] (The Hacker News)
⚡ Weekly Recap: Proxy Botnet, Office Zero-Day, MongoDB Ransoms, AI Hijacks & New Threats – The Hacker News

Every week brings new discoveries, attacks, and defenses that shape the state of cybersecurity. Some threats are stopped quickly, while others go unseen until they cause real damage. Sometimes a single update, exploit, or mistake changes how we think about risk and protection. Every incident shows how defenders adapt — and how fast attackers try … Read More “⚡ Weekly Recap: Proxy Botnet, Office Zero-Day, MongoDB Ransoms, AI Hijacks & New Threats – The Hacker News” »
Russia-linked hacking group Fancy Bear is exploiting a brand-new vulnerability in Microsoft Office, CERT-UA says – Read More –
The phrase “Move fast and break things” is a guiding philosophy in the technology industry. The phrase was coined by Meta CEO and founder Mark Zuckerberg more than two decades ago: an operational directive for Facebook developers to prioritize speed and innovation even at the cost of stability. “Unless you are breaking stuff,” Zuckerberg told … Read More “We moved fast and broke things. It’s time for a change. – CyberScoop” »
Bitdefender has discovered a new Android malware campaign that uses Hugging Face – Read More –
The maintainer of Notepad++ has revealed that state-sponsored attackers hijacked the utility’s update mechanism to redirect update traffic to malicious servers instead. “The attack involved [an] infrastructure-level compromise that allowed malicious actors to intercept and redirect update traffic destined for notepad-plus-plus.org,” developer Don Ho said. “The compromise occurred at the hosting – Read More – … Read More “Notepad++ Official Update Mechanism Hijacked to Deliver Malware to Select Users – The Hacker News” »
Linwei Ding, a former Google engineer, has been found guilty of stealing trade secrets for China – Read More –
The update infrastructure for eScan antivirus, a security solution developed by Indian cybersecurity company MicroWorld Technologies, has been compromised by unknown attackers to deliver a persistent downloader to enterprise and consumer systems. “Malicious updates were distributed through eScan’s legitimate update infrastructure, resulting in the deployment of multi-stage malware to enterprise – Read More – The … Read More “eScan Antivirus Update Servers Compromised to Deliver Multi-Stage Malware – The Hacker News” »
Cybersecurity researchers have disclosed details of a supply chain attack targeting the Open VSX Registry in which unidentified threat actors compromised a legitimate developer’s resources to push malicious updates to downstream users. “On January 30, 2026, four established Open VSX extensions published by the oorzc author had malicious versions published to Open VSX that embed … Read More “Open VSX Supply Chain Attack Used Compromised Dev Account to Spread GlassWorm – The Hacker News” »
Why should renters like me have to trade away our privacy just to get a roof over our heads? | Samantha Floreani – Data and computer security | The Guardian

The rise in real estate tech means renters often hand over huge amounts of revealing information to digital third parties – at great risk Get our breaking news email, free app or daily news podcast Would you trade your data privacy and security for housing? Thanks to the rise in real estate technologies, renters often … Read More “Why should renters like me have to trade away our privacy just to get a roof over our heads? | Samantha Floreani – Data and computer security | The Guardian” »
Real estate agents in Australia using apps that leave millions of lease documents at risk, digital researcher says – Data and computer security | The Guardian

‘This is a blatant and disturbing disregard for the law and for people’s security,’ digital rights advocate says Get our breaking news email, free app or daily news podcast Australian platforms used by real estate agents to upload documentation for renters and landlords are leaving people’s personal information exposed in hyperlinks accessible online. An analysis … Read More “Real estate agents in Australia using apps that leave millions of lease documents at risk, digital researcher says – Data and computer security | The Guardian” »
Ransomware victims surged in Q4 2025 despite fewer active extortion groups, with data leaks rising 50%, ReliaQuest researchers report – Read More –
Ransomware victims surged in Q4 2025 despite fewer active extortion groups, with data leaks rising 50%, ReliaQuest researchers report – Read More –
US Seizes $400 Million Linked to Helix Dark Web Crypto Mixer – Hackread – Cybersecurity News, Data Breaches, AI, and More

US authorities take control of over $400 million in crypto, cash, and property tied to Helix, a major darknet bitcoin mixing service used by drug markets. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Windows Malware Uses Pulsar RAT for Live Chats While Stealing Data – Hackread – Cybersecurity News, Data Breaches, AI, and More
We usually think of computer viruses as silent, invisible programs running in the background, but a worrying discovery shows that modern hackers are getting much more personal. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Juice Jacking Continues to Be a Cyber Problem in South Africa – Da Vinci Cybersecurity: Leading Cyber Security Services in South Africa.

“Juice jacking” may be a new term for some, but it has been around as a method of cyber attack for a long time. The former problem was that it was expensive to install, but now that has all changed. The tools required for juice jacking have become cheaper and easier and it’s now a … Read More “Juice Jacking Continues to Be a Cyber Problem in South Africa – Da Vinci Cybersecurity: Leading Cyber Security Services in South Africa.” »
A Farsi-speaking threat actor aligned with Iranian state interests is suspected to be behind a new campaign targeting non-governmental organizations and individuals involved in documenting recent human rights abuses. The activity, observed by HarfangLab in January 2026, has been codenamed RedKitten. It’s said to coincide with the nationwide unrest in Iran that began towards the … Read More “Iran-Linked RedKitten Cyber Campaign Targets Human Rights NGOs and Activists – The Hacker News” »
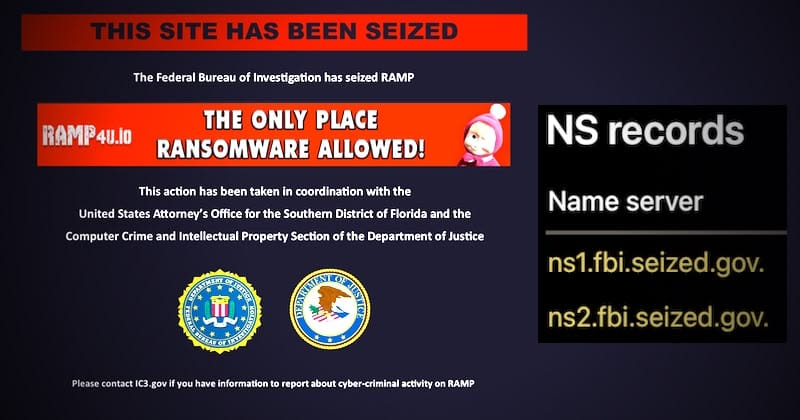
The FBI has seized control of RAMP, a notorious cybercrime online forum that bragged to be the only place that allowed ransomware, and boasted over 14,000 active users. Now some of those users’ details are likely to be in the hands of the police… Read more in my article on the Bitdefender blog. – Read … Read More “FBI takes notorious RAMP ransomware forum offline – GRAHAM CLULEY” »
Former Google Engineer Convicted of Stealing AI Secrets for China – Hackread – Cybersecurity News, Data Breaches, AI, and More

A 38 year old was convicted on seven counts of economic espionage and seven counts of theft of trade secrets following an 11 day trial. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Mandiant Finds ShinyHunters-Style Vishing Attacks Stealing MFA to Breach SaaS Platforms – The Hacker News

Google-owned Mandiant on Friday said it identified an “expansion in threat activity” that uses tradecraft consistent with extortion-themed attacks orchestrated by a financially motivated hacking group known as ShinyHunters. The attacks leverage advanced voice phishing (aka vishing) and bogus credential harvesting sites mimicking targeted companies to gain unauthorized access to victim – Read More – … Read More “Mandiant Finds ShinyHunters-Style Vishing Attacks Stealing MFA to Breach SaaS Platforms – The Hacker News” »
CERT Polska, the Polish computer emergency response team, revealed that coordinated cyber attacks targeted more than 30 wind and photovoltaic farms, a private company from the manufacturing sector, and a large combined heat and power plant (CHP) supplying heat to almost half a million customers in the country. The incident took place on December 29, … Read More “CERT Polska Details Coordinated Cyber Attacks on 30+ Wind and Solar Farms – The Hacker News” »
A trio of domains that allegedly distributed pirated content, including movies, TV shows, video games and other content was seized by the U.S. government as part of a globally coordinated crackdown on copyright infringement, the Justice Department said Friday. The sites — zamunda.net, arenabg.com and zelka.org — were among the most popular domains in Bulgaria … Read More “DOJ seizes piracy sites, Italian police dismantle illegal IPTV operation – CyberScoop” »
Arsink Spyware Posing as WhatsApp, YouTube, Instagram, TikTok Hits 143 Countries – Hackread – Cybersecurity News, Data Breaches, AI, and More

Another day, another Android malware campaign targeting unsuspecting users worldwide by masquerading as popular apps. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Millions of devices used as proxies by cybercriminals, espionage groups and data thieves have been removed from circulation following Google’s disruption of IPIDEA, a China-based residential proxy network. The reduction in available proxy devices came after Google’s Threat Intelligence Group used legal action and intelligence sharing to target the company’s domain infrastructure, Google said in … Read More “Google’s disruption rips millions out of devices out of malicious network – CyberScoop” »
CrowdStrike assessed that two new threat actor groups have spun off from North Korean Labyrinth Chollima hackers – Read More –
Non-profit ITRC says the number of data breaches increased 5% annually to reach a record total in 2025 – Read More –
Researchers Uncover Chrome Extensions Abusing Affiliate Links and Stealing ChatGPT Access – The Hacker News

Cybersecurity researchers have discovered malicious Google Chrome extensions that come with capabilities to hijack affiliate links, steal data, and collect OpenAI ChatGPT authentication tokens. One of the extensions in question is Amazon Ads Blocker (ID: pnpchphmplpdimbllknjoiopmfphellj), which claims to be a tool to browse Amazon without any sponsored content. It was uploaded to the Chrome … Read More “Researchers Uncover Chrome Extensions Abusing Affiliate Links and Stealing ChatGPT Access – The Hacker News” »
Cybersecurity researchers have discovered a new campaign attributed to a China-linked threat actor known as UAT-8099 that took place between late 2025 and early 2026. The activity, discovered by Cisco Talos, has targeted vulnerable Internet Information Services (IIS) servers located across Asia, but with a specific focus on targets in Thailand and Vietnam. The scale … Read More “China-Linked UAT-8099 Targets IIS Servers in Asia with BadIIS SEO Malware – The Hacker News” »
The RedKitten campaign distributes lures designed to target people seeking information about missing persons or political dissidents in Iran – Read More –
Behind the scenes of law enforcement in cyber: what do we know about caught cybercriminals? What brought them in, where do they come from and what was their function in the crimescape? Introduction: One view on the scattered fight against cybercrime The growing sophistication and diversification of cybercrime have compelled law enforcement agencies worldwide to … Read More “Badges, Bytes and Blackmail – The Hacker News” »
Cyber fraudsters targeting corporate finance departments costs businesses millions a year – Read More –
Much of the public conversation about the U.S. “winning” the AI race with China centers exclusively on each nations’ ability to develop and implement leading AI models. But amid escalating cyber threats, the rising reality is that the race will not be won merely by the nation with the most advanced technology, but the one … Read More “Cybersecurity can be America’s secret weapon in the AI race – CyberScoop” »
Multiple vulnerabilities have been discovered in Ivanti Endpoint Manager Mobile which could allow for remote code execution. Ivanti Endpoint Manager Mobile is a mobile management software engine that enables IT to set policies for mobile devices, applications and content. Successful exploitation of these vulnerabilities could allow for remote code execution in the context of the … Read More “Multiple Vulnerabilities in Ivanti Endpoint Manager Mobile Could Allow for Remote Code Execution – Cyber Security Advisories – MS-ISAC” »
SmarterTools has addressed two more security flaws in SmarterMail email software, including one critical security flaw that could result in arbitrary code execution. The vulnerability, tracked as CVE-2026-24423, carries a CVSS score of 9.3 out of 10.0. “SmarterTools SmarterMail versions prior to build 9511 contain an unauthenticated remote code execution vulnerability in the ConnectToHub API … Read More “SmarterMail Fixes Critical Unauthenticated RCE Flaw with CVSS 9.3 Score – The Hacker News” »
Ex-Google Engineer Convicted for Stealing 2,000 AI Trade Secrets for China Startup – The Hacker News

A former Google engineer accused of stealing thousands of the company’s confidential documents to build a startup in China has been convicted in the U.S., the Department of Justice (DoJ) announced Thursday. Linwei Ding (aka Leon Ding), 38, was convicted by a federal jury on seven counts of economic espionage and seven counts of theft … Read More “Ex-Google Engineer Convicted for Stealing 2,000 AI Trade Secrets for China Startup – The Hacker News” »
The Middle East and Africa (MEA) region is experiencing a rapid industrial change. The use of Operational Technology (OT)… The post OT & IoT Security in MEA: Why Industrial Cyber Risks Are Surging appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
Ivanti has rolled out security updates to address two security flaws impacting Ivanti Endpoint Manager Mobile (EPMM) that have been exploited in zero-day attacks, one of which has been added by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to its Known Exploited Vulnerabilities (KEV) catalog. The critical-severity vulnerabilities are listed below – CVE-2026-1281 (CVSS … Read More “Two Ivanti EPMM Zero-Day RCE Flaws Actively Exploited, Security Updates Released – The Hacker News” »
Imagine the scene. It’s a cold Monday morning in Moscow. You walk out to your car, coffee in hand, ready to face the day. You press the button to unlock your car, and … nothing happens. You try again. Still nothing. The alarm starts blaring. You can’t turn it off. Read more in my article … Read More “Hacking attack leaves Russian car owners locked out of their vehicles – GRAHAM CLULEY” »
CVE-2025-12758: Unicode Variation Selectors Bypass in ‘validator’ library (isLength) – Full Disclosure

Posted by Karol Wrótniak on Jan 29 Summary ======= A vulnerability was discovered in the popular JavaScript library ‘validator’. The isLength() function incorrectly handles Unicode Variation Selectors (U+FE0E and U+FE0F). An attacker can inject thousands of these zero-width characters into a string, causing the library to report a much smaller perceived length than the … Read More “CVE-2025-12758: Unicode Variation Selectors Bypass in ‘validator’ library (isLength) – Full Disclosure” »
Posted by Andrey Stoykov on Jan 29 Hi. I would like to publish my paper for exploiting XAMPP installations. Thanks, Andrey – Read More – Full Disclosure
Posted by Andrey Stoykov on Jan 29 # Exploit Title: Elgg – Lack of Password Complexity # Date: 1/2026 # Exploit Author: Andrey Stoykov # Version: 6.3.3 # Tested on: Ubuntu 22.04 # Blog: https://msecureltd.blogspot.com/2026/01/friday-fun-pentest-series-48-weak.html // HTTP Request – Changing Password POST /action/usersettings/save HTTP/1.1 Host: elgg.local User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:148.0) … Read More “Weak Password Complexity – elggv6.3.3 – Full Disclosure” »
Posted by Andrey Stoykov on Jan 29 # Exploit Title: Elgg – Username Enumeration # Date: 1/2026 # Exploit Author: Andrey Stoykov # Version: 6.3.3 # Tested on: Ubuntu 22.04 # Blog: https://msecureltd.blogspot.com/2026/01/friday-fun-pentest-series-47-lack-of.html // HTTP Request – Resetting Password – Valid User POST /action/user/requestnewpassword HTTP/1.1 Host: elgg.local User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; … Read More “Username Enumeration – elggv6.3.3 – Full Disclosure” »
The ‘staggering’ cybersecurity weakness that isn’t getting enough focus, according to a top Secret Service official – CyberScoop

The internet domain registration system is a major weakness that malicious hackers can exploit, but is often being overlooked, a senior Secret Service official said Thursday. “It is staggering to me that we live in a world where domain registrars and registrars will do bulk registration of various spellings of a major institution’s brand name … Read More “The ‘staggering’ cybersecurity weakness that isn’t getting enough focus, according to a top Secret Service official – CyberScoop” »
A new joint investigation by SentinelOne SentinelLABS, and Censys has revealed that the open-source artificial intelligence (AI) deployment has created a vast “unmanaged, publicly accessible layer of AI compute infrastructure” that spans 175,000 unique Ollama hosts across 130 countries. These systems, which span both cloud and residential networks across the world, operate outside the – … Read More “Researchers Find 175,000 Publicly Exposed Ollama AI Servers Across 130 Countries – The Hacker News” »
Following a federal raid on Fulton County, Georgia’s Elections Office, lawmakers and state election officials sharply criticized the Trump administration, accusing the White House of chasing baseless internet conspiracy theories about fraud in the 2020 election. Officials also warned the raid could set a precedent for similar federal actions targeting the 2026 midterm elections. According … Read More “Lawmakers, election officials blast Trump administration after Fulton County raid – CyberScoop” »
The U.S. government wants the rest of the world to adopt its artificial intelligence cybersecurity standards, a top official with the Office of the National Cyber Director said Thursday. As part of an effort to advance American AI, the administration will be “undertaking diplomacy efforts to promote American AI cybersecurity standards and norms, establishing industry … Read More “US wants to push its view of AI cybersecurity standards to the rest of the world – CyberScoop” »
Op Bizarre Bazaar: New LLMjacking Campaign Targets Unprotected Models – Hackread – Cybersecurity News, Data Breaches, AI, and More

Pillar Security Research has discovered Operation Bizarre Bazaar, a massive cyberattack campaign led by a hacker known as Hecker. Between December 2025 and January 2026, over 35,000 sessions were recorded targeting AI systems to steal compute power and resell access via silver.inc. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Common Cloud Migration Security Mistakes (and How to Avoid Them) – Hackread – Cybersecurity News, Data Breaches, AI, and More

Common cloud migration security mistakes explained, from weak access controls to misconfigurations, plus practical steps organisations can take to avoid risk. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The French data protection regulator said that France Travail’s response to a 2024 data breach violated GDPR – Read More –
The FBI outlines ten actions which organizations can take to defend networks against cybercriminal and nation-state threats – Read More –