The U.S. Department of Justice (DoJ) this week announced the seizure of $61 million worth of Tether that were allegedly associated with bogus cryptocurrency schemes known as pig butchering. The confiscated funds were traced to cryptocurrency addresses used for the laundering of criminally derived proceeds stolen from victims of cryptocurrency investment scams, the department added. … Read More “DoJ Seizes $61 Million in Tether Linked to Pig Butchering Crypto Scams – The Hacker News” »
Author: [email protected] (The Hacker News)
ShinyHunters Leak 2M Records From Dutch Telecom Odido, Claim 21M Stolen – Hackread – Cybersecurity News, Data Breaches, AI and More

ShinyHunters hackers leak 2 million records from Dutch telecom Odido after ransom refusal, claiming up to 21 million customer records were stolen in the breach. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
ClawJacked Vulnerability in OpenClaw Could Let Websites Hijack AI Agents – Hackread – Cybersecurity News, Data Breaches, AI and More

Is your AI assistant safe? Oasis Security researchers have found a critical ClawJacked vulnerability in OpenClaw that allows hackers to hijack AI agents through a simple browser tab. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
The Shadowserver Foundation has revealed that over 900 Sangoma FreePBX instances still remain infected with web shells as part of attacks that exploited a command injection vulnerability starting in December 2025. Of these, 401 instances are located in the U.S., followed by 51 in Brazil, 43 in Canada, 40 in Germany, and 36 in France. … Read More “900+ Sangoma FreePBX Instances Compromised in Ongoing Web Shell Attacks – The Hacker News” »
Cybersecurity researchers have disclosed details of a malicious Go module that’s designed to harvest passwords, create persistent access via SSH, and deliver a Linux backdoor named Rekoobe. The Go module, github[.]com/xinfeisoft/crypto, impersonates the legitimate “golang.org/x/crypto” codebase, but injects malicious code that’s responsible for exfiltrating secrets entered via terminal password – Read More – The Hacker … Read More “Malicious Go Crypto Module Steals Passwords, Deploys Rekoobe Backdoor – The Hacker News” »
The security researchers from Zscaler ThreatLabz have also discovered five new tools deployed by the North Korean hacking group – Read More –
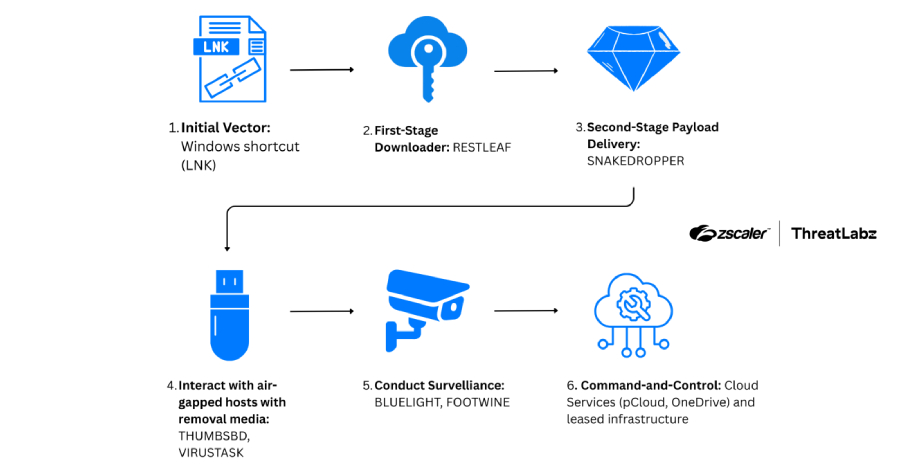
The North Korean threat actor known as ScarCruft has been attributed to a fresh set of tools, including a backdoor that uses Zoho WorkDrive for command-and-control (C2) communications to fetch more payloads and an implant that uses removable media to relay commands and breach air-gapped networks. The campaign, codenamed Ruby Jumper by Zscaler ThreatLabz, involves … Read More “ScarCruft Uses Zoho WorkDrive and USB Malware to Breach Air-Gapped Networks – The Hacker News” »
The UK government says its new Vulnerability Monitoring Service has cut unresolved security flaws by 75% and reduced cyber-attack fix times from nearly two months to just over a week – Read More –
SpaceX IPO Date Explained: Key Insights Investors Need to Know – Hackread – Cybersecurity News, Data Breaches, AI and More

Guide to the SpaceX IPO date, company profile, pricing method, risks, and how investors can prepare to buy shares when the company goes public soon. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
Hackers Use 1Campaign to Hide Malicious Ads From Google Reviewers – Hackread – Cybersecurity News, Data Breaches, AI and More

Varonis Threat Labs reveals 1Campaign, a platform used to trick Google Ads and hide phishing pages. Learn how this cloaking tool targets real users while evading security. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
International law enforcement operation led by Europol targets network of teenagers and young adults involved in ransomware attacks, extortion and other crimes – Read More –
Threat actors are luring unsuspecting users into running trojanized gaming utilities that are distributed via browsers and chat platforms to distribute a remote access trojan (RAT). “A malicious downloader staged a portable Java runtime and executed a malicious Java archive (JAR) file named jd-gui.jar,” the Microsoft Threat Intelligence team said in a post on X. … Read More “Trojanized Gaming Tools Spread Java-Based RAT via Browser and Chat Platforms – The Hacker News” »
Meta Files Lawsuits Against Brazil, China, Vietnam Advertisers Over Celeb-Bait Scams – The Hacker News

Meta on Thursday said it’s taking legal action to tackle scams on its platforms by filing lawsuits against what it calls deceptive advertisers based in Brazil, China, and Vietnam. As part of the effort, the advertisers’ methods of payment have been suspended, related accounts have been disabled, and the website domain names used to pull … Read More “Meta Files Lawsuits Against Brazil, China, Vietnam Advertisers Over Celeb-Bait Scams – The Hacker News” »
Madhu Gottumukkala is out as acting director of the Cybersecurity and Infrastructure Security Agency, with current agency executive director for cybersecurity Nick Andersen replacing him as the interim leader. News of Gottumukkala’s departure breaks one day after CyberScoop reported on widespread dismay with the agency’s performance during the first year of the Trump administration, with … Read More “Gottumukkala out, Andersen in as acting CISA director – CyberScoop” »
Madhu Gottumukkala is out as acting director of the Cybersecurity and Infrastructure Security Agency, with current agency executive director for cybersecurity Nick Andersen replacing him as the interim leader. News of Gottumukkala’s departure breaks one day after CyberScoop reported on widespread dismay with the agency’s performance during the first year of the Trump administration, with … Read More “Gottumukkala out, Andersen in as acting CISA director – CyberScoop” »
New Aeternum C2 Botnet Evades Takedowns via Polygon Blockchain – Hackread – Cybersecurity News, Data Breaches, AI and More

Qrator Research Lab has identified Aeternum C2, a botnet that uses the Polygon blockchain for commands, making it nearly impossible to shut down. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
A global law enforcement effort has taken root to combat The Com, a sprawling nihilistic network of thousands of minors and young adults engaged in various forms of cybercrime, including physical violence and extortion. Project Compass, an operation coordinated by Europol with support from 28 countries, including all members of the Five Eyes, has resulted … Read More “Project Compass is Europol’s new playbook for taking on The Com – CyberScoop” »
A new report claims that the cost of insider security incidents has surged 20% in two years, reaching an average of US $19.5 million per organization annually, with no sign that the alarming figure is flattening. Read more in my article on the Fortra blog. – Read More – GRAHAM CLULEY
A key Senate Committee moved to advance legislation that would overhaul cybersecurity practices at the Department of Health and Human Services. The bipartisan Health Care Cybersecurity and Resiliency Act sailed through the Senate Health, Education and Labor Committee Thursday on a 22-1 vote, with only Sen. Rand Paul, R-Ky., opposing it. The legislation, sponsored by … Read More “Senate moves one step closer to passing health care cyber reforms – CyberScoop” »
Fake Avast Website Targets Users With €499 Phishing Refund Scam – Hackread – Cybersecurity News, Data Breaches, AI and More
Fraudsters clone Avast’s website to target French users with a €499 phishing scam, using urgency tactics, live chat, and card validation to steal payment data. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
Aeternum C2 Botnet Stores Encrypted Commands on Polygon Blockchain to Evade Takedown – The Hacker News
Cybersecurity researchers have disclosed details of a new botnet loader called Aeternum C2 that uses a blockchain-based command-and-control (C2) infrastructure to make it resilient to takedown efforts. “Instead of relying on traditional servers or domains for command-and-control, Aeternum stores its instructions on the public Polygon blockchain,” Qrator Labs said in a report shared with The … Read More “Aeternum C2 Botnet Stores Encrypted Commands on Polygon Blockchain to Evade Takedown – The Hacker News” »
New botnet Aeternum shifted C2 operations to Polygon blockchain, complicating takedown efforts – Read More –
ThreatsDay Bulletin: Kali Linux + Claude, Chrome Crash Traps, WinRAR Flaws, LockBit & 15+ Stories – The Hacker News

Nothing here looks dramatic at first glance. That’s the point. Many of this week’s threats begin with something ordinary, like an ad, a meeting invite, or a software update. Behind the scenes, the tactics are sharper. Access happens faster. Control is established sooner. Cleanup becomes harder. Here is a quick look at the signals worth … Read More “ThreatsDay Bulletin: Kali Linux + Claude, Chrome Crash Traps, WinRAR Flaws, LockBit & 15+ Stories – The Hacker News” »
A previously undocumented threat activity cluster has been attributed to an ongoing malicious campaign targeting education and healthcare sectors in the U.S. since at least December 2025. The campaign is being tracked by Cisco Talos under the moniker UAT-10027. The end goal of the attacks is to deliver a never-before-seen backdoor codenamed Dohdoor. “Dohdoor utilizes … Read More “UAT-10027 Targets U.S. Education and Healthcare with Dohdoor Backdoor – The Hacker News” »
2025 saw 32M phishing emails, with identity threats surpassing vulnerabilities – Read More –
How to Cut MTTR by Improving Threat Visibility in Your SOC – Hackread – Cybersecurity News, Data Breaches, AI and More

How better threat visibility and real-time intelligence reduce MTTR, improve SOC response speed, and strengthen resilience through faster detection and containment. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
Report Finds Just 1% of Security Flaws Drive Most Cyberattacks in 2025 – Hackread – Cybersecurity News, Data Breaches, AI and More

New VulnCheck research reveals that while thousands of CVEs are discovered yearly, only 1% drive real-world impact. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
Entra ID OAuth Consent Can Grant ChatGPT Access to Emails – Hackread – Cybersecurity News, Data Breaches, AI and More

OAuth consent in Entra ID can grant apps like ChatGPT email access after approval, exposing hidden risks that may bypass MFA and enable persistent access. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
How to Cut MTTR by Improving Threat Visibility in Your SOC – Hackread – Cybersecurity News, Data Breaches, AI and More

How better threat visibility and real-time intelligence reduce MTTR, improve SOC response speed, and strengthen resilience through faster detection and containment. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
The UK’s Information Commissioner’s Office is about to ditch single-leader model for CEO and board in a major shake-up – Read More –
Datadog report reveals two-fifths of services are affected by exploitable bugs – Read More –
There is a certain poetic justice in a cybersecurity-related story that has emerged from Moscow this week: A man has been accused of trying to extort money… from a notorious Russian ransomware gang. Read more in my article on the Hot for Security blog. – Read More – GRAHAM CLULEY
Introduction: Steal It Today, Break It in a Decade Digital evolution is unstoppable, and though the pace may vary, things tend to fall into place sooner rather than later. That, of course, applies to adversaries as well. The rise of ransomware and cyber extortion generated funding for a complex and highly professional criminal ecosystem. The … Read More “Expert Recommends: Prepare for PQC Right Now – The Hacker News” »
UNC2814 hit 53 victims in 42 countries with novel backdoor in decade long cyber espionage operation – Read More –
Cybersecurity researchers have disclosed details of a new malicious package discovered on the NuGet Gallery, impersonating a library from financial services firm Stripe in an attempt to target the financial sector. The package, codenamed StripeApi.Net, attempts to masquerade as Stripe.net, a legitimate library from Stripe that has over 75 million downloads. It was uploaded by … Read More “Malicious StripeApi NuGet Package Mimicked Official Library and Stole API Tokens – The Hacker News” »
A “coordinated developer-targeting campaign” is using malicious repositories disguised as legitimate Next.js projects and technical assessments to trick victims into executing them and establish persistent access to compromised machines. “The activity aligns with a broader cluster of threats that use job-themed lures to blend into routine developer workflows and increase the likelihood of code – … Read More “Microsoft Warns Developers of Fake Next.js Job Repos Delivering In-Memory Malware – The Hacker News” »
The US and allies are urging Cisco Catalyst SD-WAN customers to hunt for signs of exploitation – Read More –
Multiple vulnerabilities have been discovered in Cisco Catalyst SD-WAN products, the most severe of which could allow for authentication bypass. Cisco Catalyst SD-WAN (formerly Viptela) is a secure, cloud-delivered software-defined WAN architecture that optimizes application performance by intelligently routing traffic over any combination of transport links (MPLS, broadband, LTE). Successful exploitation of the most severe … Read More “Multiple Vulnerabilities in Cisco Catalyst SD-WAN Products Could Allow for Authentication Bypass – Cyber Security Advisories – MS-ISAC” »
A newly disclosed maximum-severity security flaw in Cisco Catalyst SD-WAN Controller (formerly vSmart) and Catalyst SD-WAN Manager (formerly vManage) has come under active exploitation in the wild as part of malicious activity that dates back to 2023. The vulnerability, tracked as CVE-2026-20127 (CVSS score: 10.0), allows an unauthenticated remote attacker to bypass authentication and obtain … Read More “Cisco SD-WAN Zero-Day CVE-2026-20127 Exploited Since 2023 for Admin Access – The Hacker News” »
From Policy to Practice: How Indian Companies Can Audit Their DPDP Compliance Annually – JISA Softech Pvt Ltd

The Digital Personal Data Protection Act, 2023 (DPDP Act) in India has transformed the compliant dialogue into a policy-making enterprise to… The post From Policy to Practice: How Indian Companies Can Audit Their DPDP Compliance Annually appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
When the mysterious operator of an internet archiving-service decided to silence a curious Finnish blogger, they didn’t just send a stroppy email – they allegedly weaponised their own CAPTCHA page to launch a DDoS attack, threatened to invent an entirely new genre of AI porn, and tampered with parts of their own archive to smear … Read More “Smashing Security podcast #456: How to lose friends and DDoS people – GRAHAM CLULEY” »
Attackers have been exploiting a pair of zero-day vulnerabilities in Cisco’s network edge software for at least three years, and the global campaign is ongoing, authorities said across a series of warnings released Wednesday. The Cybersecurity and Infrastructure Security Agency issued an emergency directive about the global attacks and issued joint guidance with the Five … Read More “Governments issue warning over Cisco zero-day attacks dating back to 2023 – CyberScoop” »
Cybersecurity researchers have discovered four malicious NuGet packages that are designed to target ASP.NET web application developers to steal sensitive data. The campaign, discovered by Socket, exfiltrates ASP.NET Identity data, including user accounts, role assignments, and permission mappings, as well as manipulates authorization rules to create persistent backdoors in victim applications. – Read More – … Read More “Malicious NuGet Packages Stole ASP.NET Data; npm Package Dropped Malware – The Hacker News” »
Why Intelligent Contract Solutions Are Replacing Traditional CLM Systems – Hackread – Cybersecurity News, Data Breaches, AI and More

Intelligent contract solutions replace traditional CLM by adding AI analysis, benchmarking, and risk insights that speed reviews, reduce delays, and improve decisions. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
US Sanctions Russian Exploit Broker Over Stolen US Cyber Tools – Hackread – Cybersecurity News, Data Breaches, AI and More

The US Treasury targets Sergey Zelenyuk and his firm Operation Zero for the illegal trade of stolen government cyber tools following the sentencing of Peter Williams. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
ShinyHunters Claims Odido NL and Ben.nl Breach as Company Confirms Cyberattack – Hackread – Cybersecurity News, Data Breaches, AI and More

ShinyHunters claims 21 million records stolen in Odido NL and Ben.nl data breach as telecom company confirms cyberattack impacting customer contact system data. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
Google on Wednesday disclosed that it worked with industry partners to disrupt the infrastructure of a suspected China-nexus cyber espionage group tracked as UNC2814 that breached at least 53 organizations across 42 countries. “This prolific, elusive actor has a long history of targeting international governments and global telecommunications organizations across Africa, Asia, and the Americas,” … Read More “Google Disrupts UNC2814 GRIDTIDE Campaign After 53 Breaches Across 42 Countries – The Hacker News” »
Cybersecurity researchers have disclosed multiple security vulnerabilities in Anthropic’s Claude Code, an artificial intelligence (AI)-powered coding assistant, that could result in remote code execution and theft of API credentials. “The vulnerabilities exploit various configuration mechanisms, including Hooks, Model Context Protocol (MCP) servers, and environment variables – executing – Read More – The Hacker News
Triage is supposed to make things simpler. In a lot of teams, it does the opposite. When you can’t reach a confident verdict early, alerts turn into repeat checks, back-and-forth, and “just escalate it” calls. That cost doesn’t stay inside the SOC; it shows up as missed SLAs, higher cost per case, and more room … Read More “Top 5 Ways Broken Triage Increases Business Risk Instead of Reducing It – The Hacker News” »
The notorious cybercrime collective known as Scattered LAPSUS$ Hunters (SLH) has been observed offering financial incentives to recruit women to pull off social engineering attacks. The idea is to hire them for voice phishing campaigns targeting IT help desks, Dataminr said in a new threat brief. The group is said to be offering anywhere between … Read More “SLH Offers $500–$1,000 Per Call to Recruit Women for IT Help Desk Vishing Attacks – The Hacker News” »