Google said Wednesday that it caught suspected People’s Republic of China-backed hackers leveraging its Calendar service to help stealthily stage attacks on government agencies.
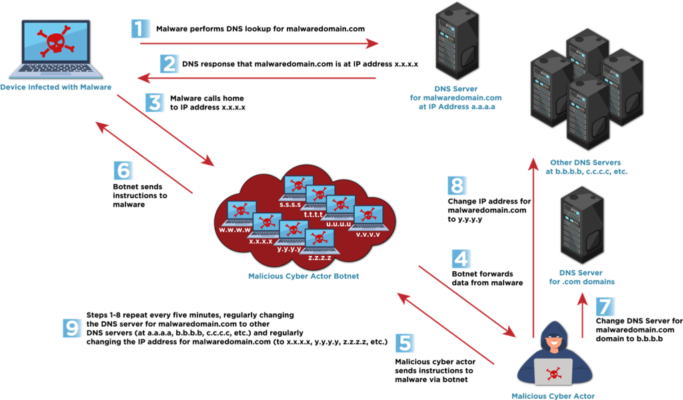
In late October of last year, Google Threat Intelligence Group said it “discovered an exploited government website hosting malware being used to target multiple other government entities,” the company’s Patrick Whitsell wrote in a blog post. The exploited website delivered malware the company dubbed TOUGHPROGRESS that took advantage of Google Calendar for command and control (C2) to help it blend in with authentic activity.
Google determined “with high confidence” that the group behind the attacks was APT41, the Chinese Ministry of State Security-linked outfit alternatively known by a host of other names such as Wicked Panda, Winnti and Double Dragon.
“To disrupt APT41 and TOUGHPROGRESS malware, we have developed custom fingerprints to identify and take down attacker-controlled Calendars,” Whitsell wrote. “We have also terminated attacker-controlled Workspace projects, effectively dismantling the infrastructure that APT41 relied on for this campaign. Additionally, we updated file detections and added malicious domains and URLs to the Google Safe Browsing blocklist.”
There are signs that hacker exploitation of Google Calendar has been on the uptick. And APT41 has been increasingly on the radar since 2019 for going after a wide range of industries and sectors, from government to entertainment to technology to automotive targets. In 2020, the Justice Department charged seven individuals in a hacking campaign that it linked to APT41 and that it said hit hundreds of targets in the United States and elsewhere.
In the latest case, as Google explained in the blog post, APT41 delivered the malware payload through spearphishing emails hosted on the exploited government site, along with phony files and decoy PDFs. TOUGHPROGRESS has the ability to read and write events via an attacker-controlled Google Calendar, Google said. It involves placing encrypted commands on specific past dates, polling the Calendar for those events and decrypting events, then again encrypting command execution to write back to another Calendar event.
“Misuse of cloud services for C2 is a technique that many threat actors leverage in order to blend in with legitimate activity,” Whitsell wrote.
The Chinese government denies all claims of connections to any hacking groups.
The post Chinese hackers used Google Calendar to aid attacks on government entities appeared first on CyberScoop.
–
Read More – CyberScoop