HYPR is latest firm to reveal hiring of fraudulent IT worker overseas – djohnson
– [[{“value”:”
The problem of fake remote tech workers attempting to gain employment at Western companies has been in the news quite a bit these days. Quite a bit.
But this problem may not be restricted to North Korean operatives, and more and more organizations are stepping up to reveal their own encounters with fake IT employees, while sounding an alarm that companies need to invest more attention and resources into how they vet remote and contract employees.
Executives from HYPR, an identity security company, revealed this week that they recently offered a contract to a software engineer claiming to be from Eastern Europe. This person initially accepted the job before walking away when the onboarding and verification process raised a number of red flags about their true identity and location.
Ryan Rowcliffe, field chief technology officer for HYPR, told CyberScoop that the employee came from a contracting agency they had used in the past, meaning “there was some level of inherent trust” about the credibility of the proposed candidates.
The candidate initially sailed through the interview process, which included nearly half a dozen meetings with engineers at the company.
“The interviews went great. The individual was stellar, which is why he was given an offer,” said Rowcliffe, later adding that “this wasn’t just an IT employee; this contractor was going to be a developer resource, which means they were going to get access to intellectual property and to” the company’s software build environment.
Rowcliffe said HYPR now believes the person they spoke with on camera in those interviews was a fraudulent proxy working on behalf of the individual they were about to bring onboard.
Anton Gurov, HYPR’s chief information security officer, published a blog on the incident Thursday, providing insight into just how much legwork is required to sniff out an imposter.
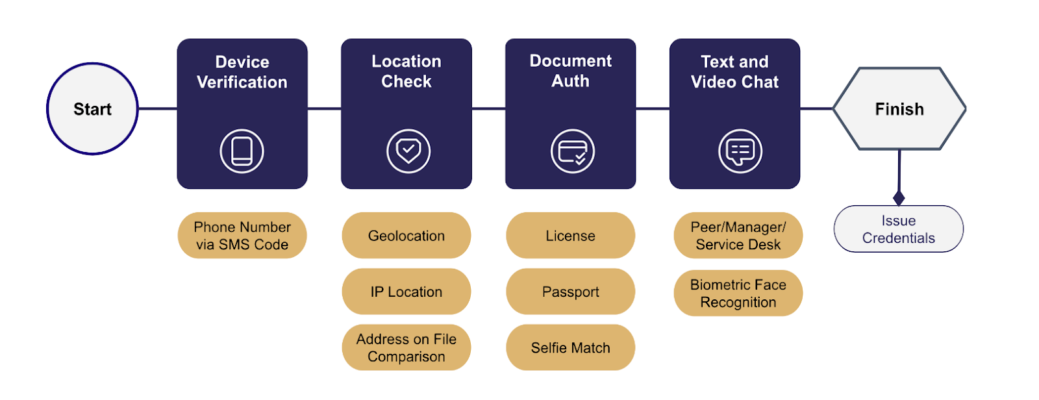
According to Gurov, the unnamed individual’s first day of onboarding was Oct. 17, where they were subjected to a battery of verification tests before they could be issued credentials. This included verification of the individual’s passport, a live facial verification test, location test and device verification.
A graphic depicting HYPR’s onboarding verification process (Source: HYPR)
That process wound up confirming some aspects of the new hire’s background, but raised the first in an escalating series of inconsistencies about their true identity.
To start, a location check of the verified phone number used by the worker revealed that they were hundreds of miles away from their listed residence. When the individual was encouraged to repeat the technical onboarding process, the location check showed a completely different IP location and browser language.
While the actual passport passed a document review, the company found “discrepancies” when comparing the passport photo to the worker’s face scan. When the company attempted to do a live video verification check, the person claimed to be experiencing technical difficulties that prevented them from showing up on camera.
At that point, the individual seemed to realize the game was up, and a day later informed HYPR they had decided to pursue another opportunity and no longer intended to take the job.
Rowcliffe said the company is not naming the individual because it is possible that some elements of their cover identity were stolen or taken from real people, and sharing the identity could potentially re-victimize those individuals.
While there’s no evidence tying this fraudulent hire to North Korea, HYPR’s story comes amid rising concerns and reports of U.S. and Western companies being targeted by fake employees from North Korea, who pose as remote IT or tech employees in an attempt to dupe companies and gain both employment or access to sensitive company data.
In many cases, the fake hires are simply seeking to earn more lucrative paychecks that can then be routed back to their homeland to fund military and nuclear weapons programs. In other instances, the workers have been observed trying to install malware on company laptops, exfiltrate sensitive information or attempt to ransom the company’s data back to them.
Rowcliffe said he doesn’t know if the person they hired was simply looking to “slow roll a paycheck” or had more nefarious intentions, but the incident highlighted just how much rigor is required today to spot fake employees overseas. While the fraud was ultimately uncovered before the employee was issued any credentials, Rowcliffe said HYPR is exploring additions to its vetting process “to find additional risk signals during the onboarding phase.”
“I don’t think we’re going to change our position on how we interview people, because we still need [our] teams to validate them. … But I think the criticality is the last line of defense is before you issue that credential,” he said.
Rowcliffe said the company’s decision to go public with its experience was partly inspired by a similar disclosure of cybersecurity company KnowBe4 about its own incident with a fake North Korean IT worker earlier this year.
Acknowledging your company was duped into hiring a fraudulent worker can be embarrassing, but these schemes are clearly working, and the more companies that share their experiences, the better that industry can adjust and adapt its vetting of overseas employees and third-party contractors.
“It’s a risky thing, right? It’s like, ‘hey, we had some sort of vulnerability happen to us,’” Rowcliffe said. “People worry about the shaming of it and I think in [this] age of transparency and security that having more businesses advocate and speak up on this” is important.
The post HYPR is latest firm to reveal hiring of fraudulent IT worker overseas appeared first on CyberScoop.
“}]] – Read More – CyberScoop

